What is SIEM?
April 24, 2018

SIEM (Security Information and Event Management) is a security and auditing system comprised of different monitoring and analysis components. The recent rise in cyber attacks, together with tighter security regulations required from organizations, are making SIEM a standard security approach which is being adopted by an increasing amount of organizations.
But what does SIEM actually involve? What are the different components that it is comprised of? How does SIEM actually help in mitigating attacks? This article seeks to provide a SIEM 101 of sorts. Follow up articles will dive deeper into some of the solutions that can be used to actually implement SIEM.
Let’s get started.
Why do we need SIEM?
There is no debate about the fact that attacks on computer systems are constantly on the rise. Coinmining, DDoS, ransomware, malware, botnets, phishing — this is just a partial list of the threats those fighting the good fight today are facing.
Interestingly enough, and as Symantec’s 2018 Internet Security Threat report points out, it’s not just the amount of attacks that is on the rise but also the avenues and methodologies used:
“From the sudden spread of WannaCry and Petya/NotPetya, to the swift growth in coinminers, 2017 provided us with another reminder that digital security threats can come from new and unexpected sources. With each passing year, not only has the sheer volume of threats increased, but the threat landscape has become more diverse, with attackers working harder to discover new avenues of attack and cover their tracks while doing so.”
System and network monitoring has always played a crucial role in helping organizations protect themselves from these attacks, and a number of related methodologies and techniques have evolved over the years. What has quickly become apparent though, is that the changing nature of cybercrime means that some attacks will often go unnoticed. Data fusion, i.e. the aggregation of data from multiple data sources and correlation between different events, has become critical, as well as the ability to retain this data for lengthy time periods.
The growth in cyber attacks has resulted in turn in tighter compliance requirements. Health Insurance Portability and Accountability Act (HIPAA), the Payment Card Industry Data Security Standard (PCI DSS), the Sarbanes-Oxley Act (SOX), and the General Data Protection Regulation (GDPR) — all these require organizations to implement a comprehensive set of security controls, including monitoring, auditing and reporting, all of which are facilitated by a SIEM system.
Definitions and evolution
Put simply, SIEM is a security system comprised of multiple monitoring and analysis components meant to help organizations detect threats and mitigate them.
As implied above, SIEM combines a number of other security disciplines and tools under one comprehensive umbrella:
- Log management (LMS) – tools used for traditional log collection and storage.
- Security Information Management (SIM) – tools or systems focusing on collecting and managing security-related data from multiple data sources. These data sources could be, for example, firewalls, DNS servers, routers, antivirus apps.
- Security Event Management (SEM) – systems that are based on proactive monitoring and analysis, including data visualization, event correlation and alerting.
SIEM is the term used today for a management system that merges all of the above into one single layer that knows how to automatically collect and process information from distributed sources, store it in one centralized location, correlate between different events, and produce alerts and reports based on this information.
SIEM components
SIEM is not a single tool or application (though there are tools that help deploy a SIEM system, see below), but a set of different building blocks that all constitute part of a system. There is no standard SIEM protocol or established methodology, but most SIEM systems will comprise most if not all of the elements described in this section.
Aggregation
Representing the raw output of running processes in a digital environment, logs are the perfect source for providing an accurate picture of what is taking place in real time.
Whether firewall logs, server logs, database logs or any other type relevant as SIEM logs being generated in your environment, SIEM systems are able of collecting this data and storing it in one central location for extended retention. This collection process is usually performed by agents or applications, deployed on the monitored system and configured to forward the data to the SIEM system’s central data store.
Processing and Normalization
The biggest challenge in collecting data in the context of SIEM is overcoming the variety of log formats. A SIEM system, by its very nature, will be pulling data from a large number of layers — servers, firewalls, network routers, databases — to name just a few, each logging in a different format.
Take a look at the following example:
Aug 11 17:22:14 auth0 access denied for userId 34532 Daniel Berman 182.54.12.98 [11/Aug/2017:17:22:14 -0300] 182.54.12.98 authentication failed at login 34532 user Daniel Berman
Both log messages are reporting the same event—a failed authentication by a specific user (yours truly) and client IP. Note the difference in formatting of the timestamp field, how the user is logged and the actual message.
To enable efficient interpretation of the data across the different sources and event correlation, SIEM systems are able to normalize the logs. This normalization process involves processing the logs into a readable and structured format, extracting important data from them, and mapping the different fields they contain.
Correlation
Once collected, parsed and stored, the next step in SIEM systems is in charge of connecting the dots and correlating events from the different data sources. This correlation work is based on rules that are either provided by various SIEM tools, predefined for different attack scenarios, or created and fine-tuned by the analyst.
Put simply, a correlation rule defines a specific sequence of events that could be indicative of a breach in security. For example, a rule could be created to identify when more than x amount of requests is sent from specific IP ranges and ports within an amount of time.
The volume of data logged in environments is huge. Even small to medium-sized organizations will most likely be shipping tens of GBs of data a day. In effect, rules help condense that data into more manageable data sets by cutting through the noise and pointing at events that could potentially mean something.
Most SIEM systems also provide built-in mechanisms for producing reports. These reports can be useful for administration, auditing, or compliance reasons. For example, a daily report detailing alerts or rules triggered could be embedded into a dashboard.
From: server-1 09:12 PM (4 hours ago) to admin ------------------------------------------------ Report 'Daily report: File changes' completed. ------------------------------------------------ ->Processed alerts: 12 ->Post-filtering alerts: 32 ->First alert: 2018 Apr 11 08:21:16 ->Last alert: 2018 Apr 11 22:08:11 Top entries for 'Level': ------------------------------------------------ Severity 5 |32 | Severity 6 |3 | Top entries for 'Group': ------------------------------------------------ ossec |12 | syscheck |12 | Top entries for 'Location': ------------------------------------------------ localhost->syscheck |51 | (ubuntu) 172.32.44.12->syscheck |2 | Top entries for 'Rule': ------------------------------------------------ 554 - File added to the system. |12 | 550 - Integrity checksum changed. |24 |
*A report sent by Wazuh’s HIDS system.
Presentation
The ability to visualize data and events is another key component in SIEM systems as it allows analysts to easily view data. Dashboards containing multiple visualizations or views help identify trends, anomalies and monitor the general health or security status of an environment. Some SIEM tools will come with pre-made dashboards while others will allow users to create and fine-tune their own.
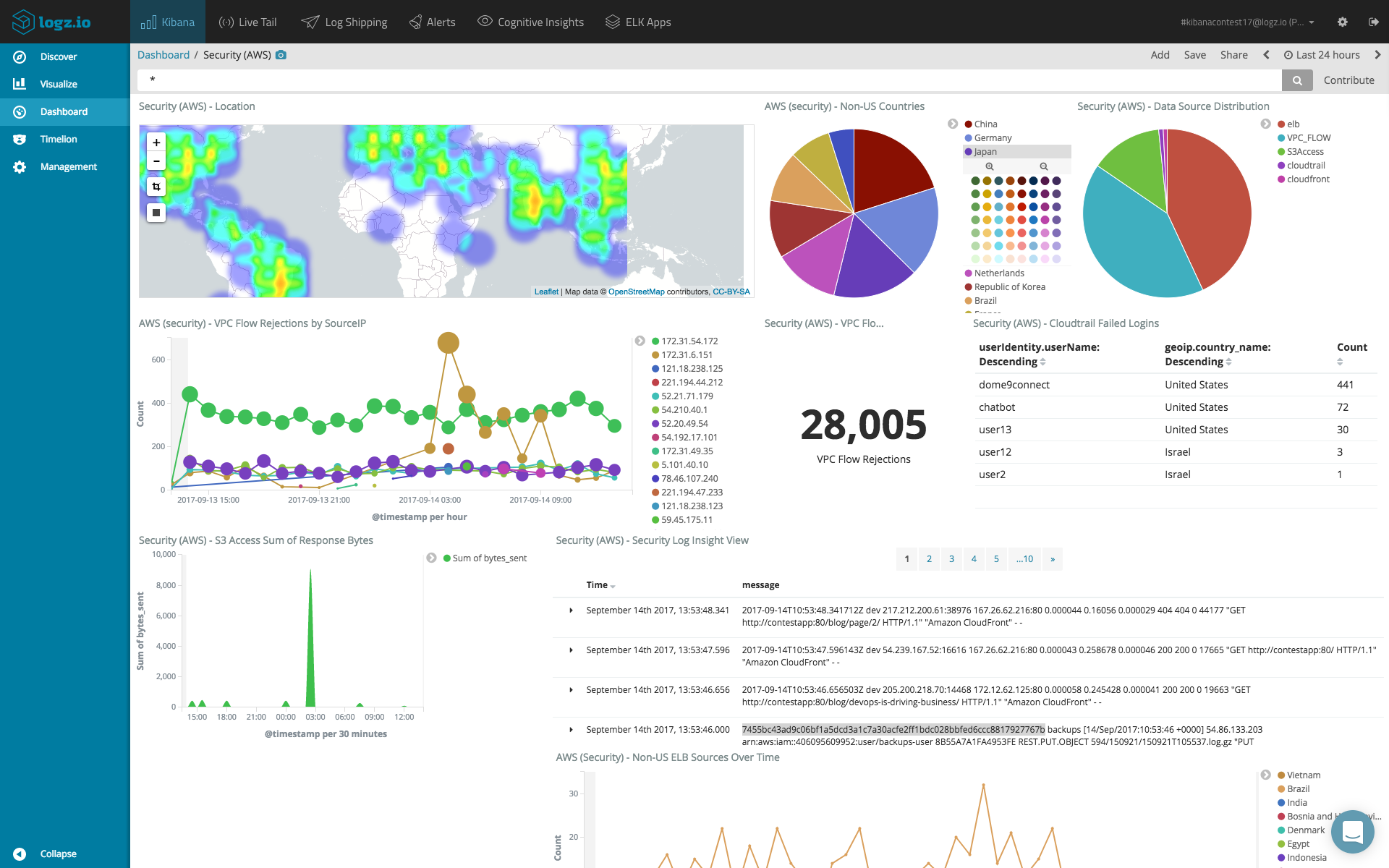
SIEM dashboard for AWS in Logz.io
Mitigation and Remediation
Once correlation rules are put in place and monitoring dashboards built to provide a comprehensive overview of the system, the last key component of a SIEM system is how incidents are handled once identified.
Most SIEM systems support mechanisms to automatically contain and mitigate security events. For example, based on correlation rules, a SIEM system can be configured to automatically begin an internal escalation process — executing scripts that begin the process of containment and passing the ball to the correct resource in the organization by triggering an alert, opening a ticket, and so forth.
So, How Does SIEM Help?
We’ve defined what SIEM is and have a general understanding of the main components comprising a SIEM system. But how does a SIEM system actually help security analysts identify and thwart attacks?
Visibility
For security analysts, SIEM systems are the focal point of the IT environment they are protecting. Centralizing the collection of security data from all relevant data sources, SIEM systems store a wealth of information that can be used to gain insight into events and processes transpiring in real time.
The degree of visibility gained is directly affected by the log aggregation and collection process put in place as part of the SIEM system. As explained above, without proper processing and parsing, log data will lack structure and will, therefore, be much more difficult to analyze.
The ability to correlate events and visualize data in dashboards is another main benefit of SIEM systems, proving analysts with a single pane of glass through which they can gain real-time visibility.
Incident Detection and Mitigation
Many events will go unnoticed by the first line of security appliances since they do not have the broader context. SIEM correlation rules, and the reporting mechanism built around them, help organizations get notified when these events are happening.
In the example of a DDoS attack, firewalls will be most likely reporting abnormal network traffic while web server requests will be reporting off-the-chart 404 responses for requests coming from a specific group of IPs.
Mitigation, in this case, could be just a matter of directing the firewall to block off traffic from those IPs, and SIEM rules can be configured to correlate between these two events and alert the relevant resource so the attack is thwarted at an early stage.
Compliance
Most compliance types today, such as HIPAA, PCI DSS, SOX and GDPR, require an organization to comply with as series of security controls. These controls include: log collection, monitoring, auditing and alerting.
Needless to say, and as must already be clear from the descriptions above, SIEM systems provide for all these articles and is one of the reasons why SIEM is becoming an industry standard for implementing security and complying.
What next?
This article was more about the theory, less about the practice. Organizations are implementing SIEM to protect their environments and to comply with a growing amount of compliance types. Once an organization has internalized the need for SIEM, the next natural stage is planning the technical implementation.
There are various tools and platforms that can be used for implementing SIEM, both proprietary (AlienVault, QRadar, LogRhythm) and open source (OSSIM, OSSEC, ELK). In future articles we will address this precise topic, outlining the different solutions and their pros and cons.
[sc_fs_multi_faq headline-0=”p” question-0=”What are SIEM rules?” answer-0=”SIEM solutions have users define the severity of events, which events should trigger alerts and at when, such as at what frequency or threshold” image-0=”” headline-1=”p” question-1=”What does a SIEM architecture have?” answer-1=”Classic SIEM architecture includes a database, correlation engine, and UI, with the engine including various agents, scanners, and detectors.” image-1=”” headline-2=”p” question-2=”Do SIEM tools use threat intelligence feeds?” answer-2=”Various threat intelligence feeds inform the correlation rules defined by SIEM users; products evaluate threat intelligence feeds differently and allow users to add their own.” image-2=”” count=”3″ html=”true” css_class=””]




