Introducing enhancements to the Logz.io Security Analytics App – RSA 2019
March 4, 2019
RSA 2019 is finally here and we’re super-excited to participate this year in this great gathering of security experts where we will be demoing Logz.io Security Analytics — our new app for helping organizations combat security threats and meet compliance requirements. More on the subject:
Logz.io Security Analytics provides a unified platform for security and operations designed for cloud and DevOps environments. It’s built on top of Logz.io’s enterprise-grade ELK Stack and is extremely easy to set up and integrate with. Advanced security features include preconfigured rules, threat intelligence and anomaly detection that together help organizations identify and mitigate threats more efficiently.
At RSA we will be showing off a series of new features and enhancements for this app that help improve incident investigation workflows and the general user experience. Below is a list of some of these features, but if you’re attending RSA and want to learn more from up close, be sure to pay us a visit at booth 2068
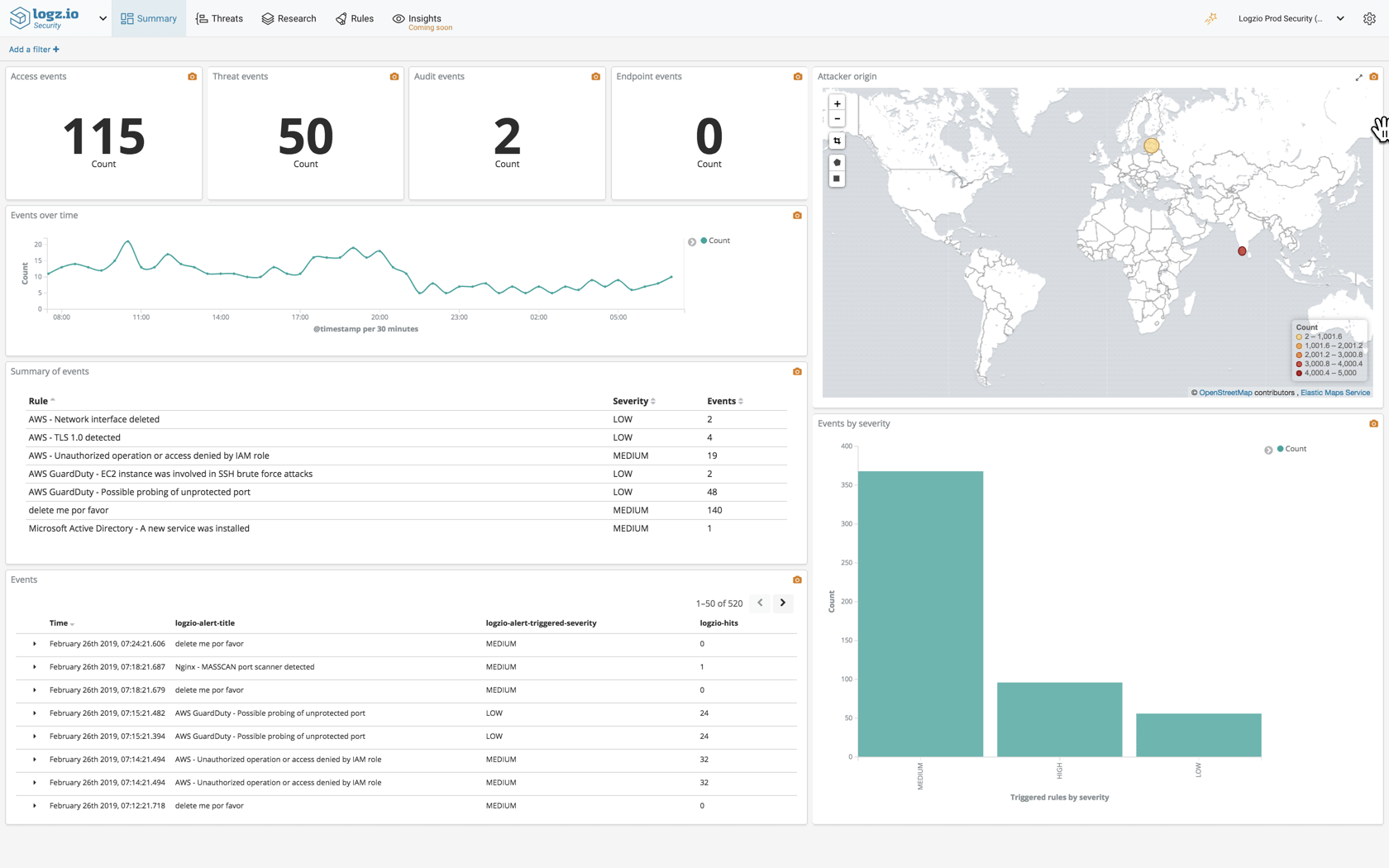
Revamped summary page
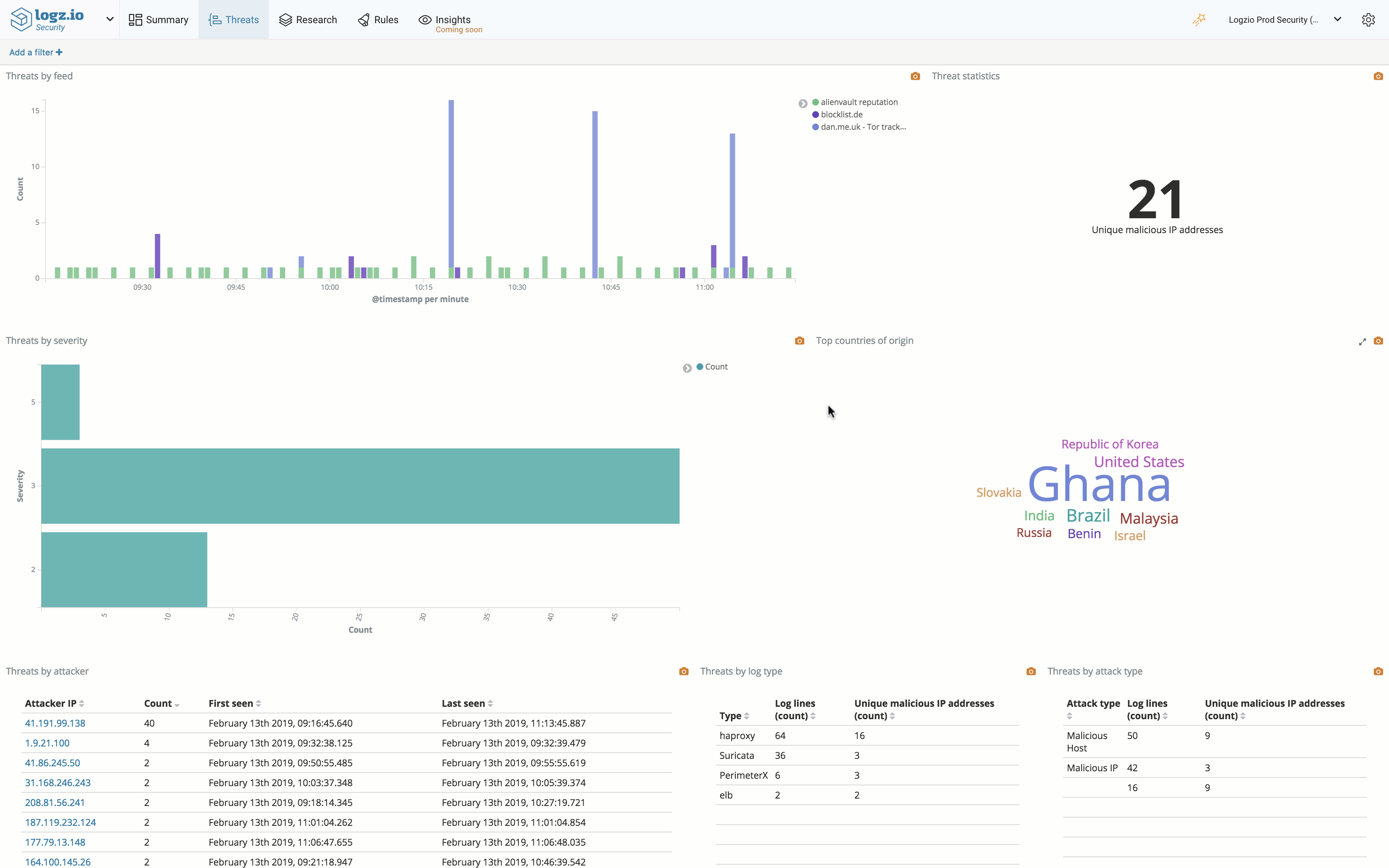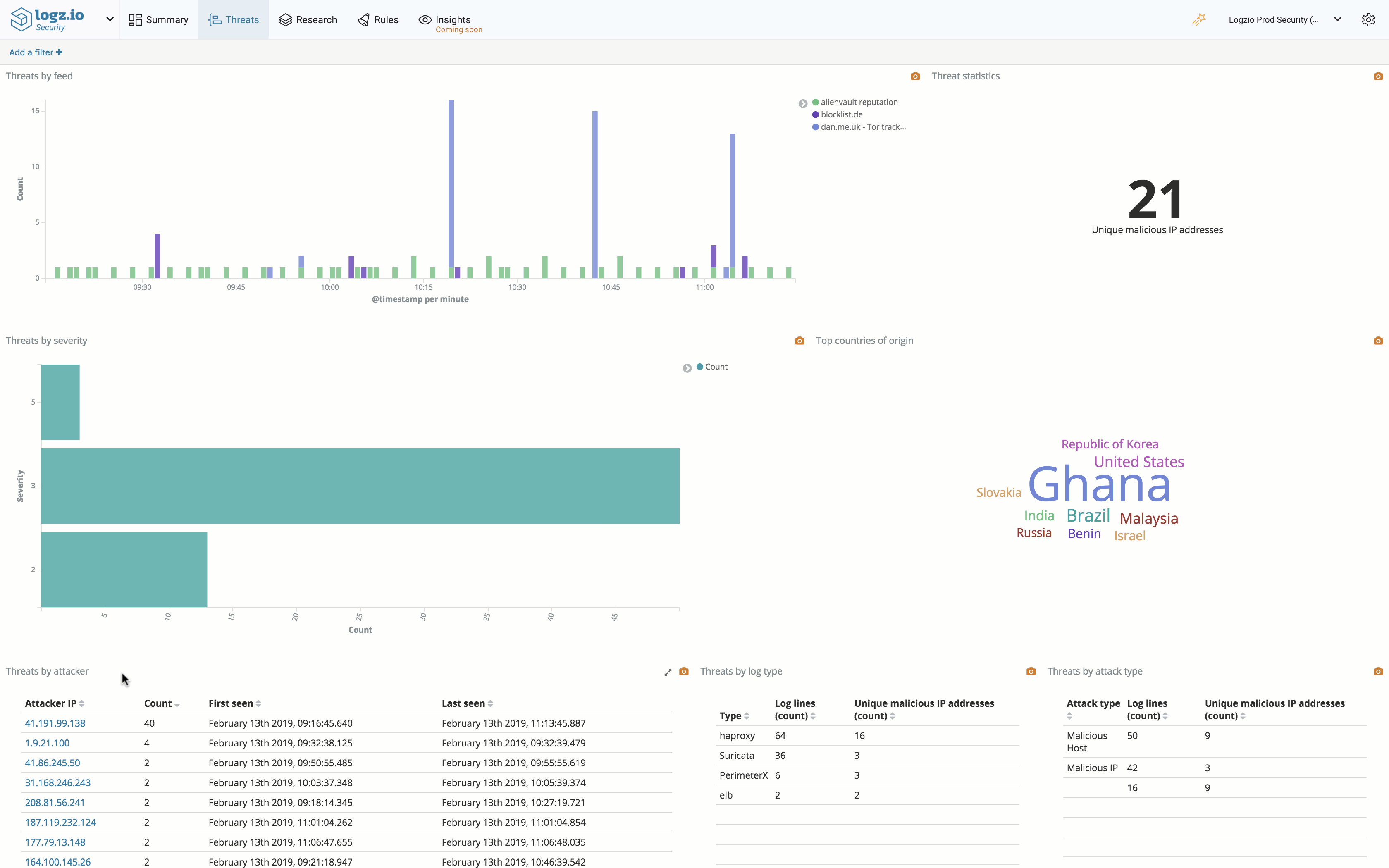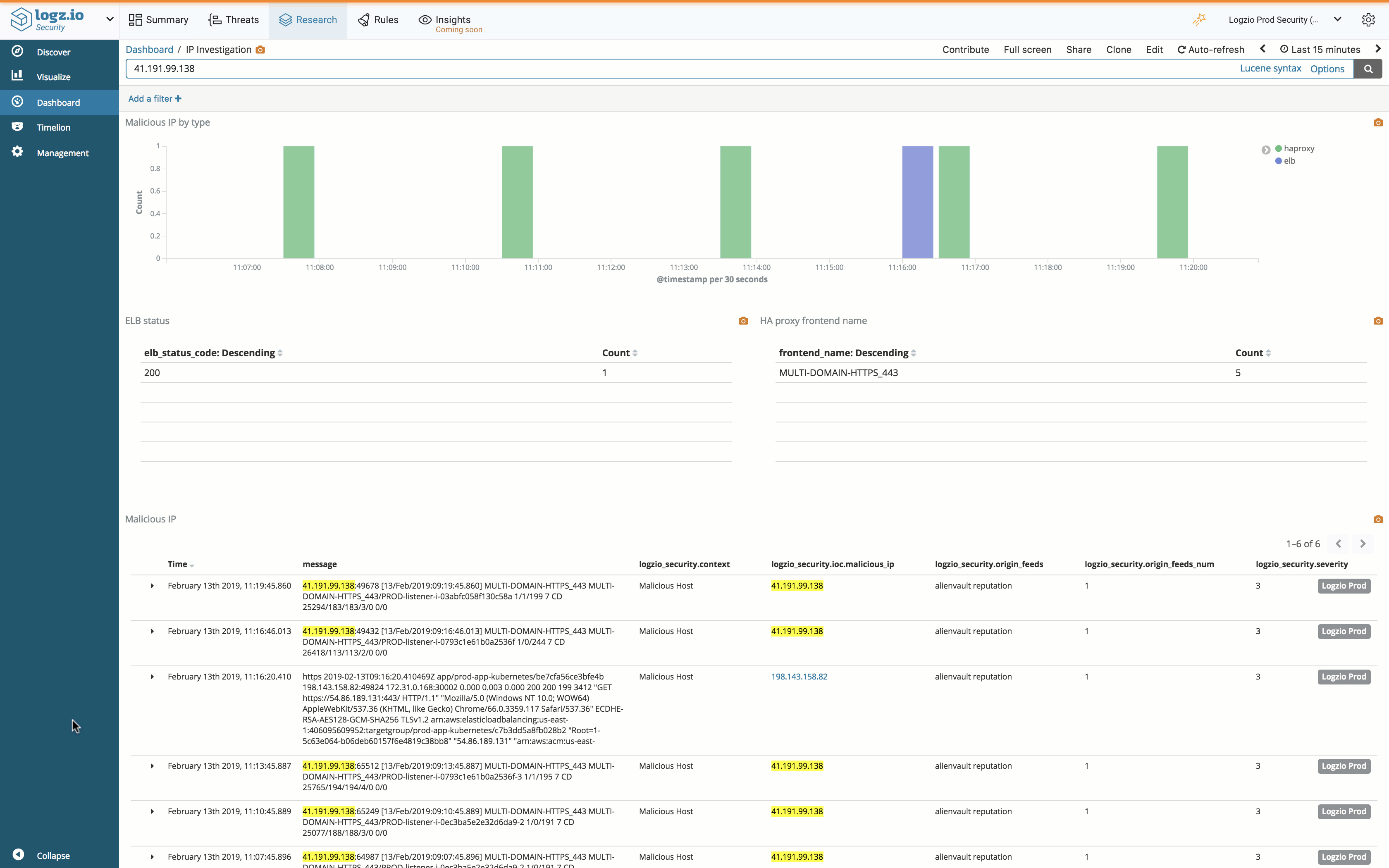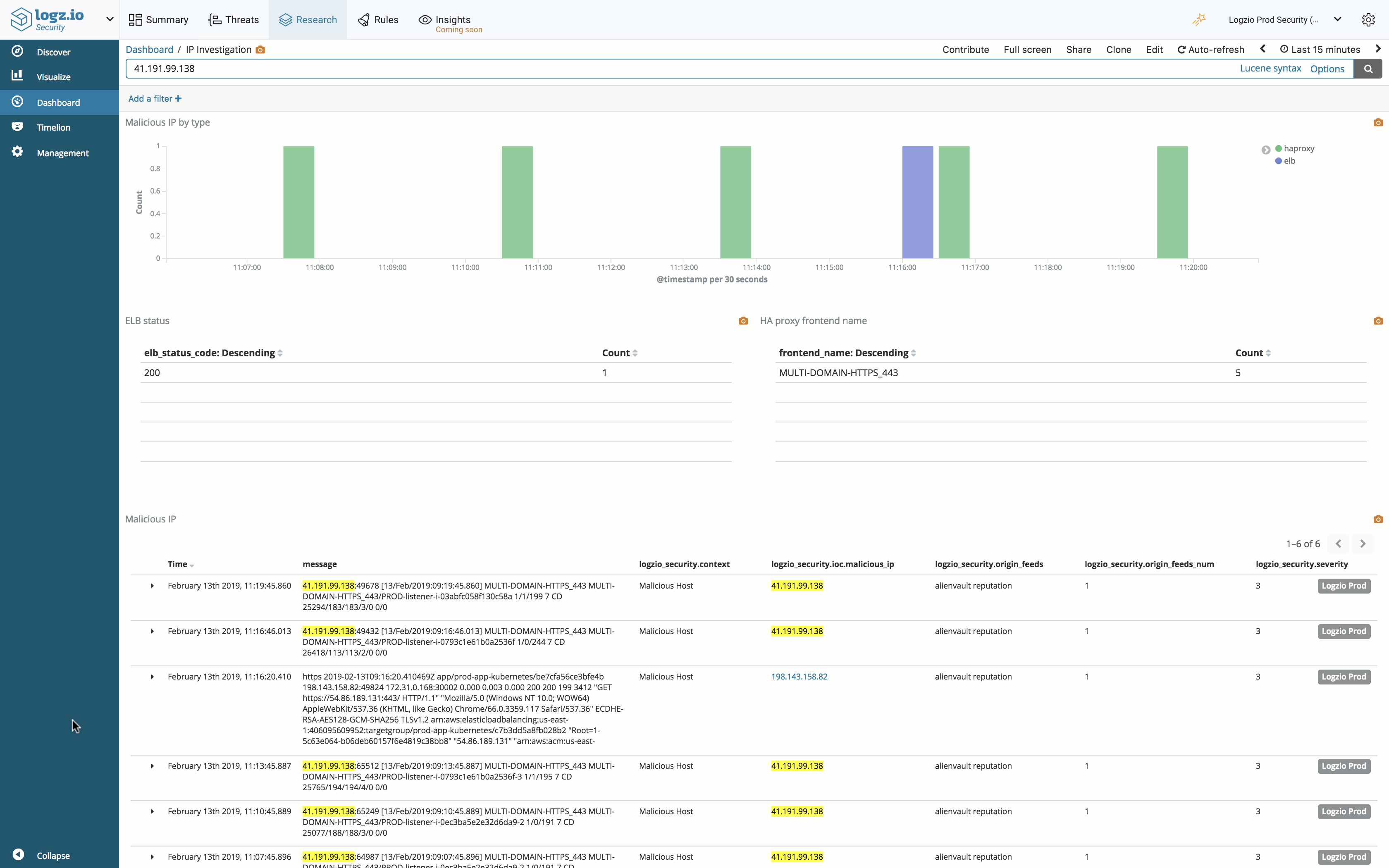
The Summary page provides you with a security overview of your environment and can be used to gauge your general security standpoint. We’ve added some enhancements to this dashboard to include detailed information on triggered rules — the number of triggered rules per category, a map showing the attack geographical origins, lists of triggered rules, and more.
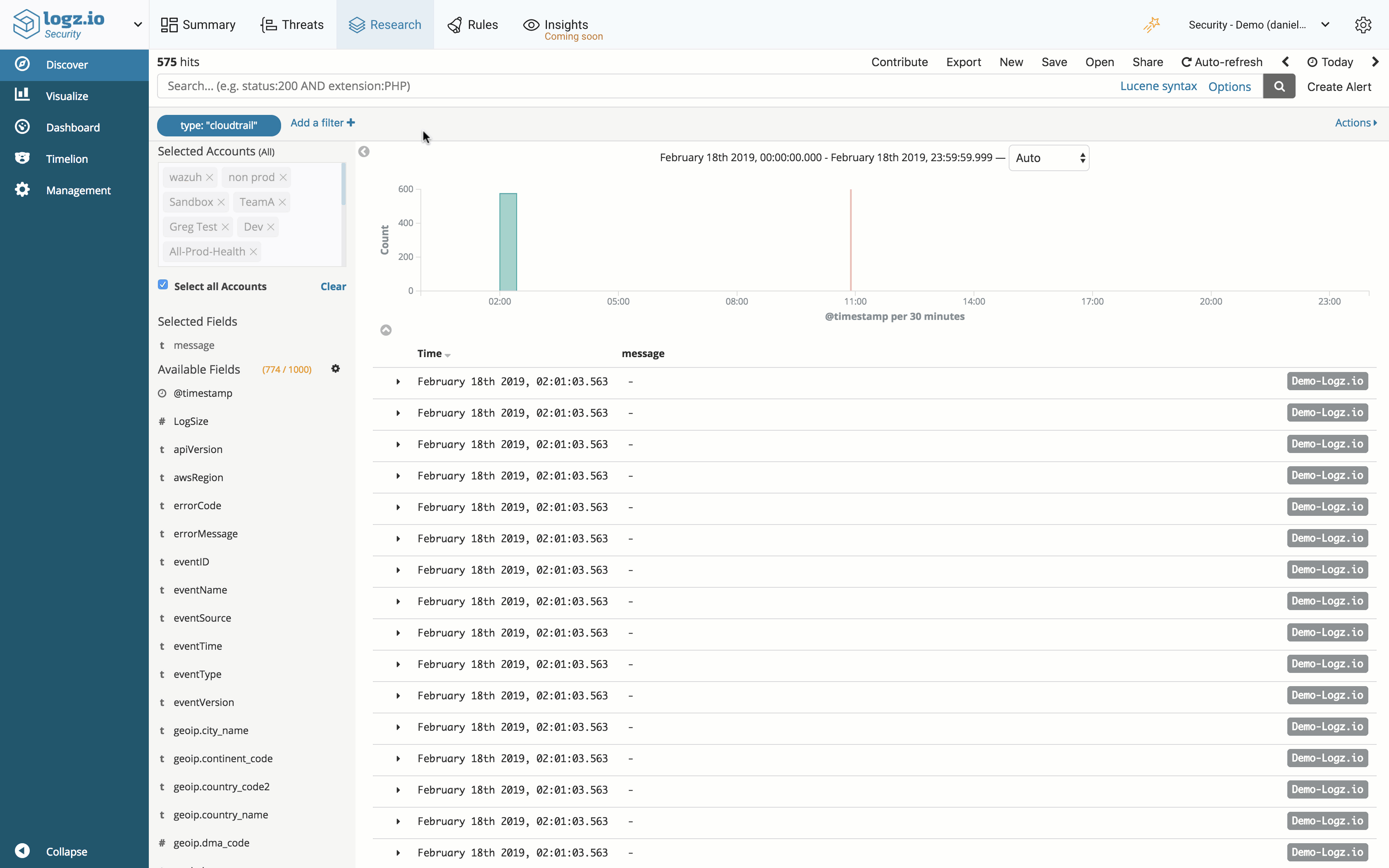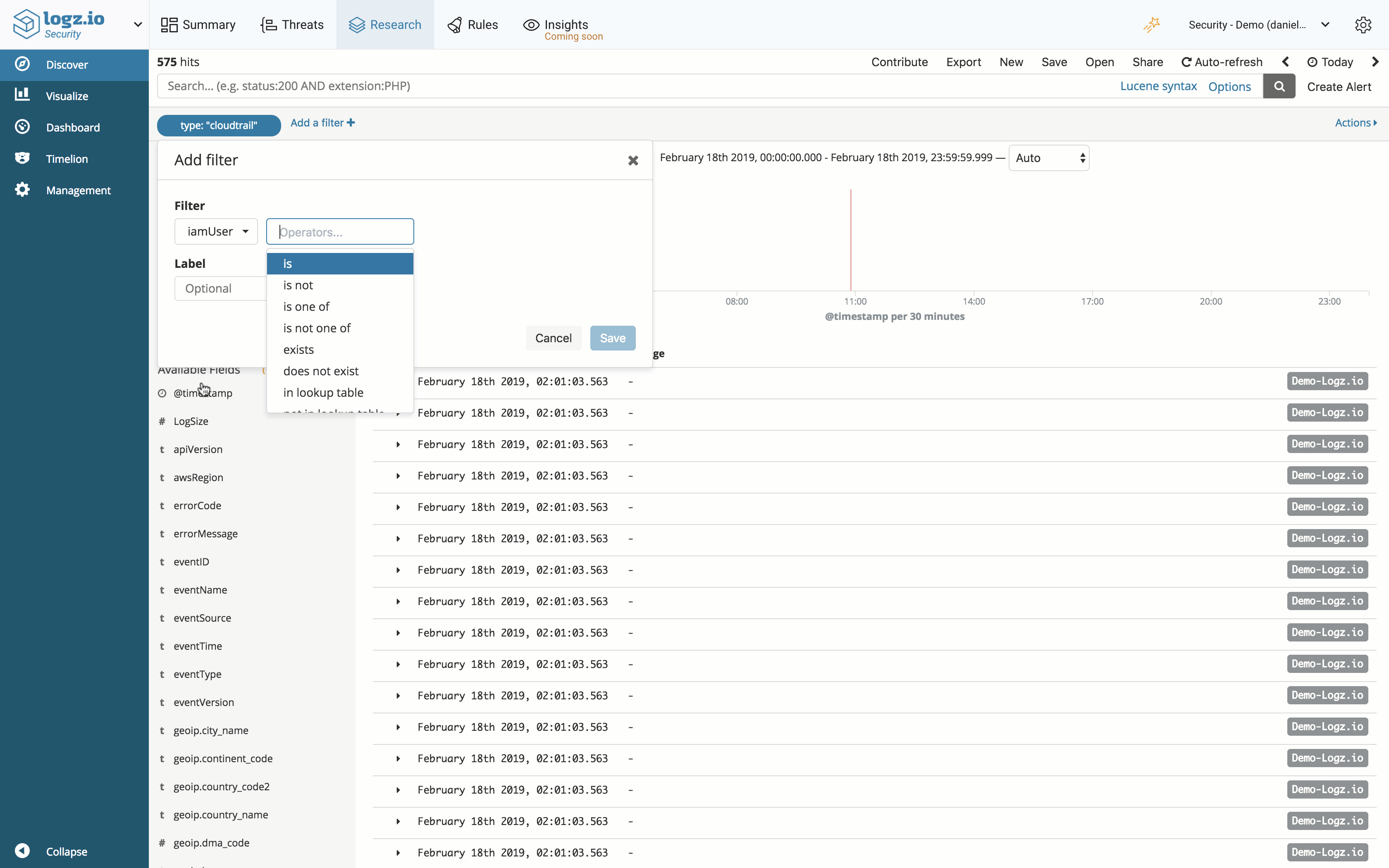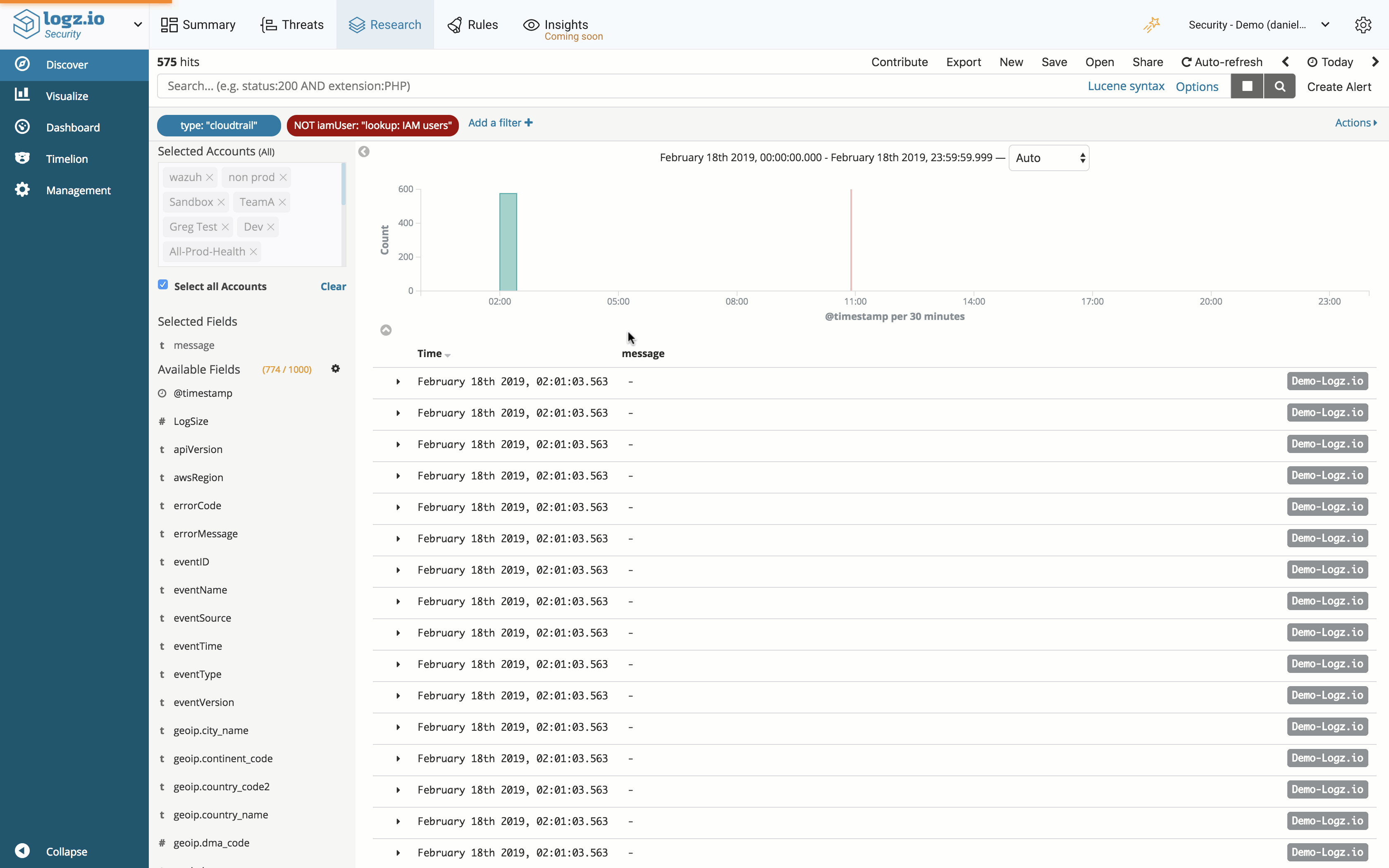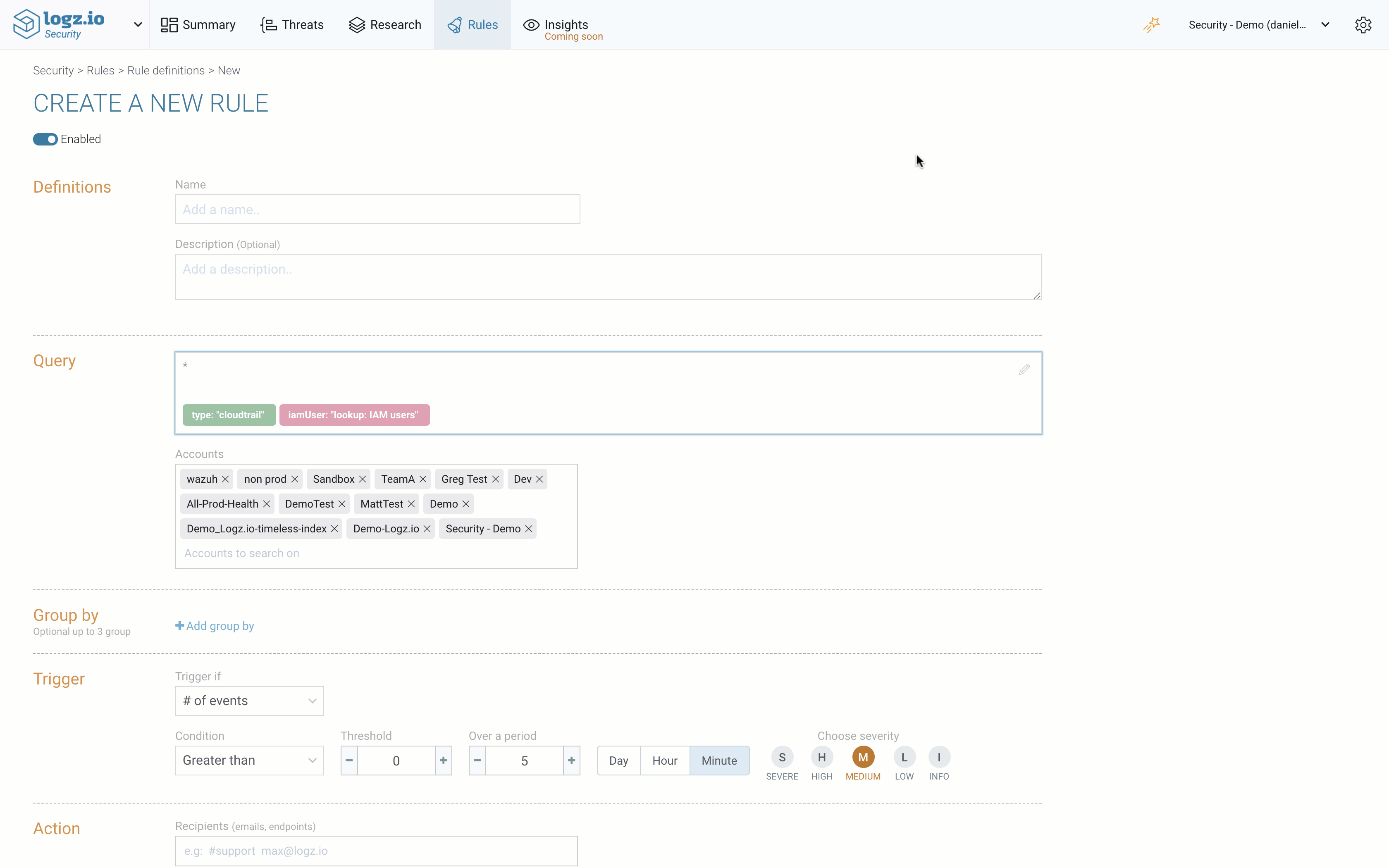
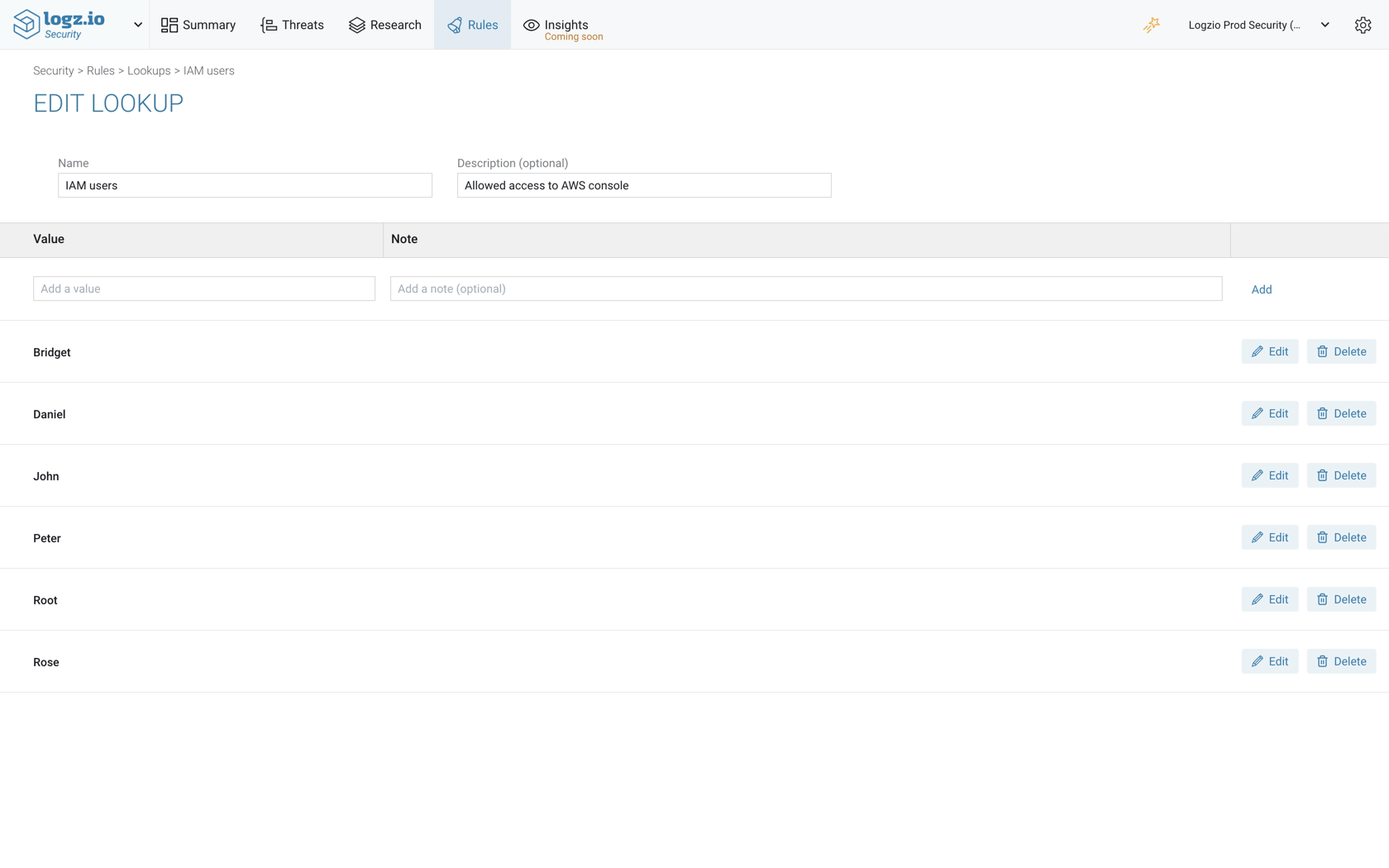
Lookups
Lookups allow you to easily create reference lists for using in Kibana queries or correlation rules.
Packaged rules and dashboards
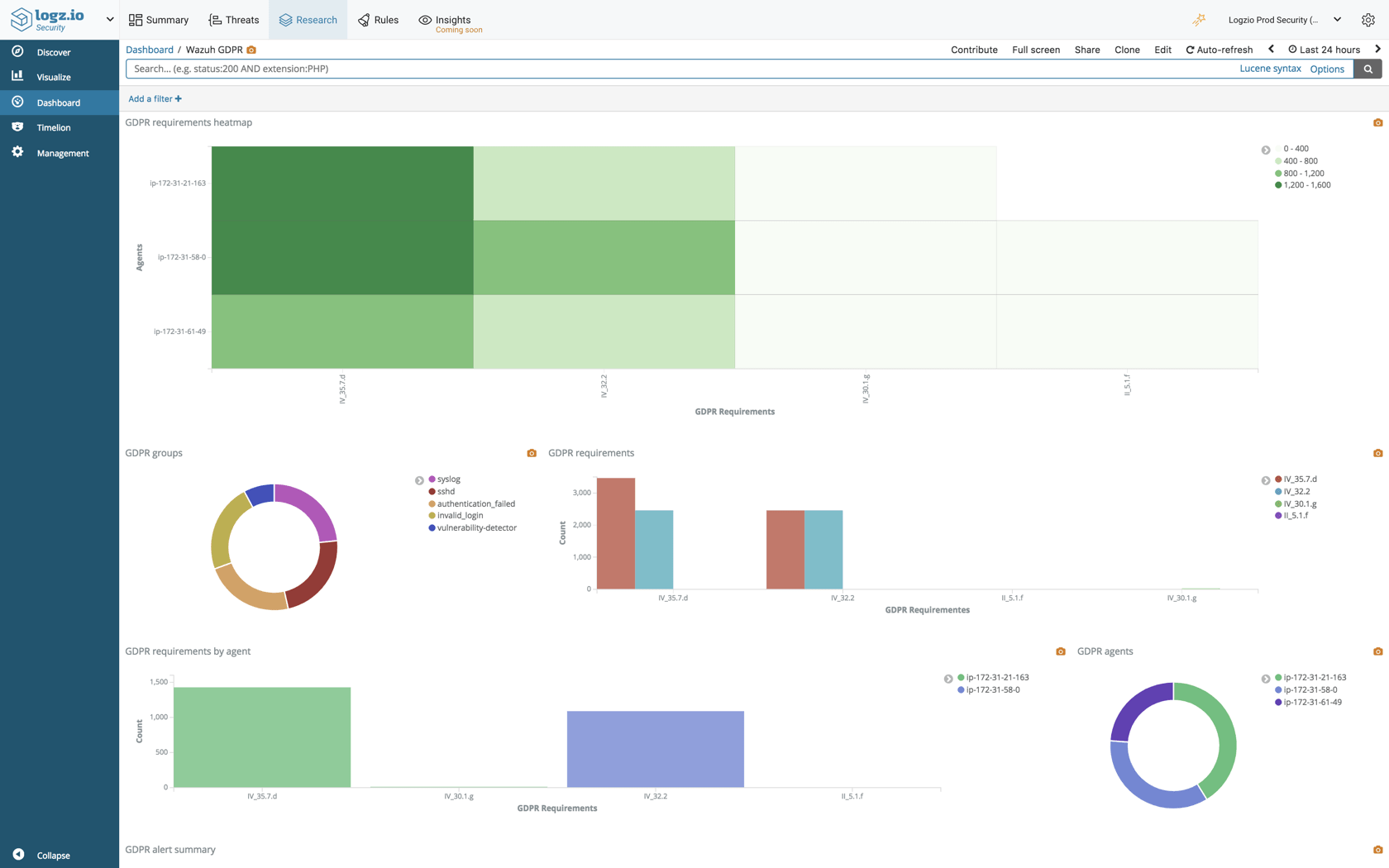
Logz.io Security Analytics ships with pre-packaged rules and security dashboards that can be used out-of-the-box for common security scenarios and use cases. We have added some new rules and dashboards, including for GDPR compliance (based on a Wazuh integration), AWS GuardDuty, Microsoft Azure Active Directory, Windows Firewall, and more.
Drilldown
To simplify investigation, we’ve added the ability in Kibana to jump from one dashboard to another.
For example, on the Threats dashboard you can see a summary on the various threats identified by the system, including a list of malicious IPs probing your network. To investigate a specific IP, you can simply click the IP in question and a dedicated dashboard is displayed, providing a more detailed picture.
Looking ahead
Offering seamless integrations, automatic scalability, threat detection, pre-packaged rules and reports and investigation tools, Logz.io Security Analytics extends the ELK Stack with security capabilities to help organizations protect their systems and meet regulatory standards.
The new features above will help make investigating security events easier. Further down the road, we will be adding some advanced forensics capabilities based on machine learning. More on this soon.
We rely heavily on our users’ feedback and so would love to hear back from you. If you are at RSA, be sure to drop by booth 2068 for a chat.