
Highlight Critical Security Attacks with Logz.io’s New Alerts Correlation

The ever-evolving cloud-native landscape creates constantly changing attack surfaces. As a result, teams implement a whole suite of security tools to identify large varieties of vulnerabilities and attacks, as well as monitor more logs than ever to find malicious activity.
But monitoring so much information can cause a barrage of notifications and alerts. Even if you’re identifying real security threats, it can be impossible to know where to start and where to focus.
Ever since Logz.io launched Cloud SIEM in 2018, we’ve been adding new capabilities to help our customers separate and prioritize critical security events from all the noise. And most recently, we’re excited to announce Alerts Correlation, which helps teams identify sequences that detect critical attacks.
More on the subject:
Identify a sequence of security events from the same user
Consider this scenario. Zeek, a popular OSS network monitoring tool, identifies a brute force attack in your environment at 10:00 PM. Since it integrates with Logz.io Cloud-Based SIEM, a rule – “Zeek – Potential SMB brute force attempt” triggers to Slack. At 10:10 PM, McAfee identifies a malware download on the same host that was subject to the brute force attack, which also triggers an alert to Logz.io.
When you view them in isolation, both alerts are of course cause for concern. But, they could easily blend in with the many other triggered alerts within that time frame. Plus, it would be difficult to tell that both attacks associate with the same host. After all, it’s time-consuming to manually sort through each alert and determine which alerts are part of the same attack.
However, if we knew that the same user in the same attack triggered these alerts, this would quickly raise the level concern, making this attack a top priority.
And that’s exactly why we built Alerts Correlation.
Logz.io Alerts Correlation identifies sequences of alerts that are associated with the same attack, raising the severity and prioritization of the security incident. With this new ability, Logz.io will look for similarities in the data of logs pertaining to two or more alerts. If a relationship is found, it will trigger a new, high severity alert.
How to Configure Alerts Correlation
Let’s configure a Correlated Alert for the scenario described above. To start, we need two alerts to identify the brute force login and the malware download. These come pre-built with Logz.io Cloud SIEM, along with many other alerts, so that part is already taken care of.
Of course, if you want to alert on events that don’t have Logz.io preconfigured rules, you can configure them yourself.
The next step is to correlate the two alerts. To do this, we’ll need to create a new alert in the Cloud SIEM interface.
Add a Filter
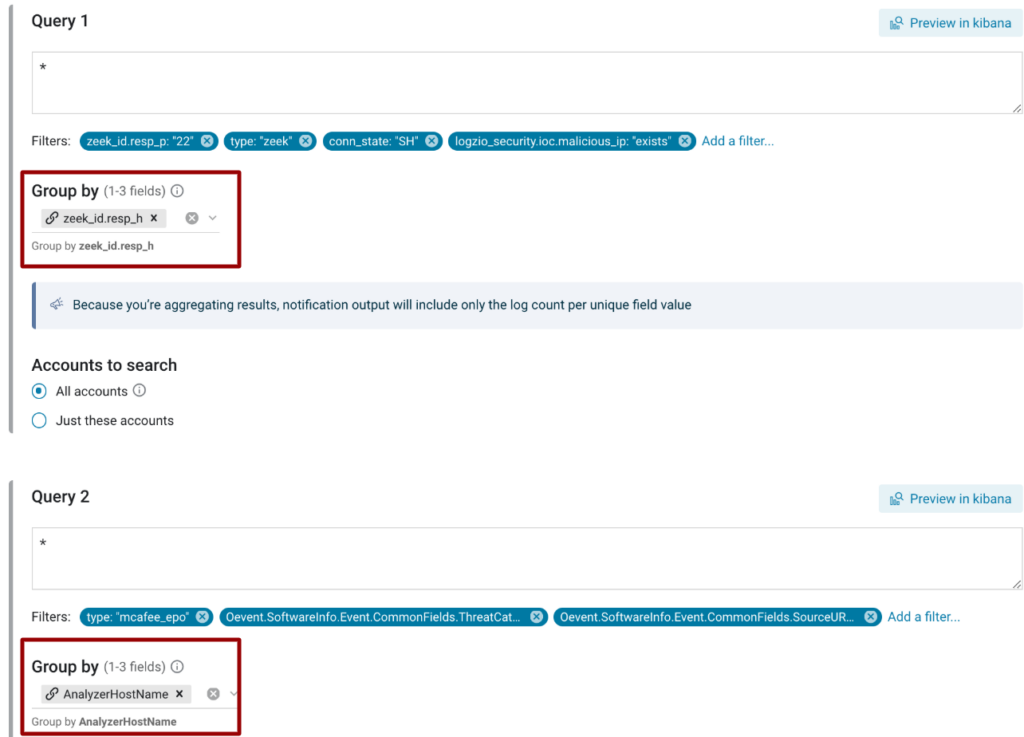
To begin configuring the correlated alert, let’s add the filters for Zeek’s ‘Brute force login’ rule into the query. Let’s also add a filter to specify that the brute force is coming from a malicious IP — which Logz.io can detect through integration with threat feeds. Next, hit ‘Add another query’ underneath the Zeek filters and add the filters for the McAfee rule that identifies the malware download. You’ll end up with two queries for the same alert.

Grouping Fields
The next step is to group the fields that would indicate the two alerts are part of the same attack. We need to do this because it’s necessary to parse these logs differently, which means they may contain the same information but sort into different fields.
For example, the username in our Zeek logs are under the field, zeek_id.resp_h, while the hostname in our McAfee logs are under the field AnalyzerHostName.
In order to know two alerts are associated with the same attack, we need to know the same user is behind the separate alerts. To do this, we can choose the fields to group the alerts in the Group by section underneath each query. If you’re familiar with SQL, this capability is like an SQL Inner Join function that looks for values that are common to both fields.
Join Queries
Next, let’s join the queries so Logz.io knows to identify common values in the fields defined in the Group by sections.

Now, if the same user is found in these separate fields when both alerts trigger, Logz.io will know that the two separate alerts connect back to the same user, surfacing the incident as a high-priority attack.
Just like any Logz.io alert, you can preview the alert trigger in Kibana, duplicate the alert, and configure it to your favorite alerting end-point.
We can view the events associated with correlated alerts in Kibana. Which specify that the Zeek and McAfee rules are part of the same alert by indicating whether the alert is associated with the first query in the correlated alert (see “Correlated security rule (1/2)”) or the second query (see “Correlated security rule (2/2)”).

Wrapping it up
With Alerts Correlation, Logz.io Cloud SIEM can surface sequences that indicate a string of malicious activities and progressing attacks. The result is that you can better prioritize high-urgency security events by automatically connecting the dots between separate alerts.
Weren’t sure if an alert for too many failed authentication attempts deserved a higher priority ranking? Try investigating the alerts immediately preceding others such as brute force logins or failed attempts from multiple IPs to identify opportunities to build correlated alerts.
Don’t have a Cloud SIEM account? Contact us and we’ll set one up for you.
Get started for free
Completely free for 14 days, no strings attached.




