Enhancing Support for Zeek (Bro) in Logz.io Security Analytics

We’re happy to announce official support for Zeek in Logz.io Security Analytics for easier security monitoring!
Logz.io Cloud Siem provides a unified platform for security and operations designed for cloud and DevOps environments. It’s built on top of Logz.io’s enterprise-grade ELK Stack and is extremely easy to set up and integrate with. Advanced security features include preconfigured rules and threat intelligence that together help organizations identify and mitigate threats more efficiently.
Zeek, formerly known as Bro, is an open-source network analysis tool used for security monitoring. When deployed, Zeek generates an extensive set of log files that contain in-depth information on a network’s activity that can be used to identify signs of suspicious activity such as port scanning or brute force logins.
Zeek has come a long way since Bro was first introduced in 2005. It has now become an extremely popular tool for security monitoring and we are now offering enhanced support for Zeek in Logz.io Security Analytics, including easy integration, new correlation rules, and a built-in monitoring dashboard.More on the subject:
Get started in mins
Installing Zeek can be a time-consuming task in and of itself without needing to spend additional time and resources on setting up a logging pipeline. Integrating with Logz.io is simple and can be done by installing Filebeat on the edge hosts in your environment.
Filebeat is an ELK-native log forwarder with an extremely small footprint and is easy to configure. In just a few steps, you’ll be able to establish a pipeline of logs from Zeek into Logz.io.
New correlation rules
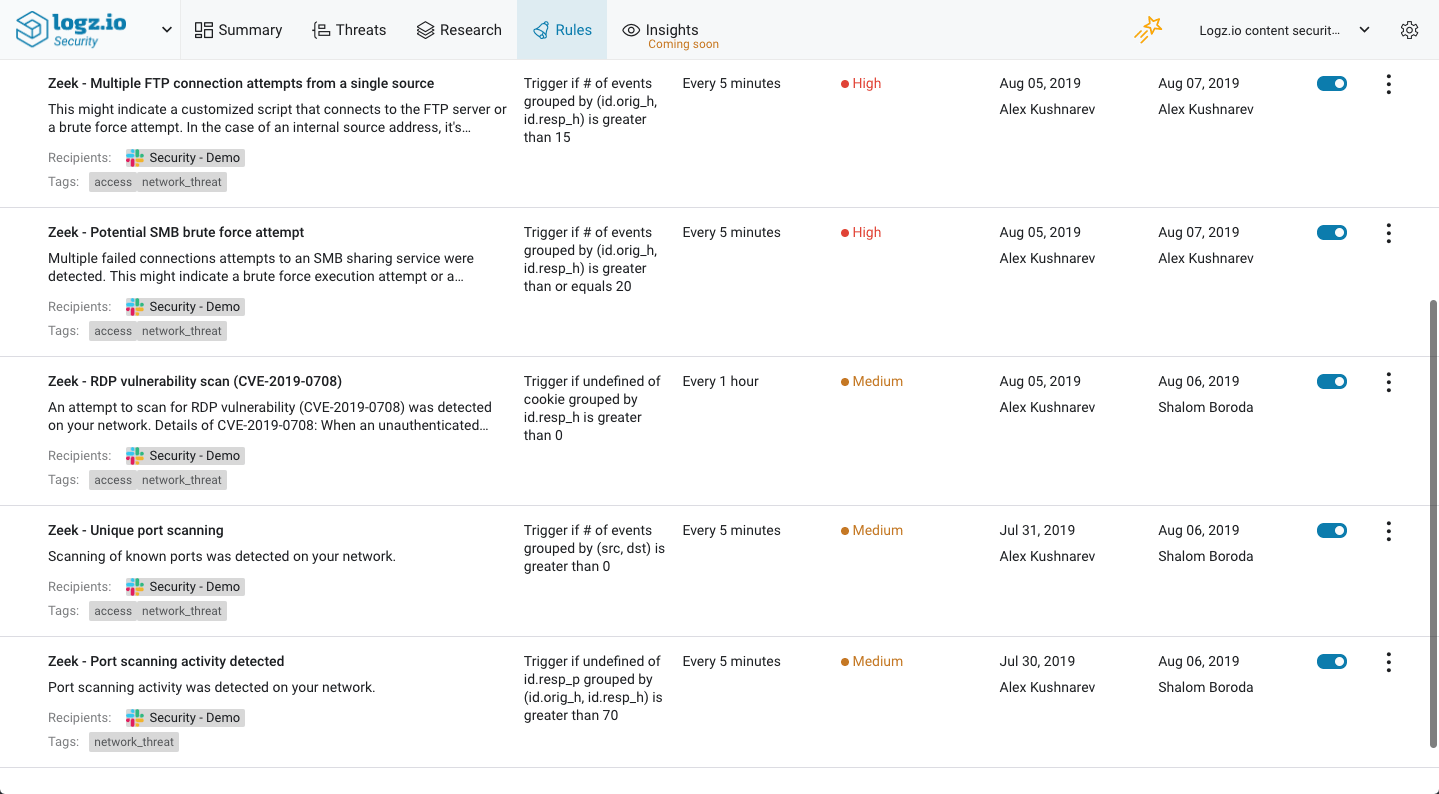
Zeek logs contain a wealth of information on potentially malicious activity. To get notified in real-time when Zeek identifies suspicious behavior, we’ve added some Zeek-specific rules that will trigger alerts when the conditions defined in these rules are met.
For example, an alert will be triggered when Zeek identifies a vulnerability scan by a user for exploitable RDP services. As the rule explains, unauthenticated RDP connections can be used to perform remote code execution and are therefore very dangerous.
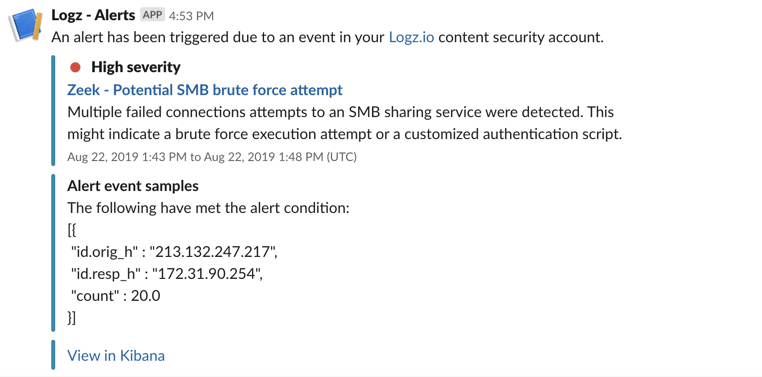
Another example is the rule identifying a potential SMB brute force attempt. Using Zeek logs, Logz.io will alert you on failed attempted connections to a shared service in your network.
As seen in these examples, Logz.io sending out these alerts via Slack but you can, of course, configure the rule to send an alert to any endpoint of your choice.
This initial batch of Zeek rules includes:
- Potential SMB brute force attempt
- Port scanning activity detected
- RDP vulnerability scan (CVE-2019-0708)
- Multiple failed SSH authentication attempts
- Multiple FTP connection attempts from a single source
- Unique port scanning
All these rules can be found together on the Rules page in Logz.io Security Analytics.
New Zeek dashboard
Based on Kibana, Logz.io Security Analytics enables you to visualize your security data in any way you like. To help you hit the ground running and to help you begin your monitoring as fast as possible, we provide canned Kibana dashboards for various security and compliance environments and scenarios. Zeek users can now use one such dashboard to monitor their network for security events!
The dashboard provides the following information:
- Alerts over time – a line chart showing the total amount of correlation rules being activated over time, both those triggering an alert and those suppressed.
- Malicious IPs – a table showing a list of malicious IPs, based on automatic correlations with public feeds such as alienvault reputation and blocklist.de.
- Malicious IPs origins – a map showing the geographical origin of malicious IPs.
- RDP users by IP chart/RDP users per IP – two visualizations displaying information on RDP users.
- Port scanning activity – a line chart showing port scanning activity identified over time.
- Rule triggering history – a line chart showing correlation rules triggered and not triggered.
- All logs – a saved search showing all Zeek logs being shipped to Logz.io.
To use this dashboard, simply go to the Dashboard page under the Research tab and look for ‘zeek’.
Endnotes
This is the first version of our support for Zeek, and it complements our existing integrations with other security monitoring tools such as OSSEC, GuardDuty, FortiGate, and Wazuh. Down the road, we plan on adding new integrations and enhancing support for existing integrations.
As usual, we’d love to hear about specific integrations and support you would like us to develop. Feel free to send us feedback and questions to: info@logz.io.
Enjoy!
Get started for free
Completely free for 14 days, no strings attached.