What Is a DDoS Attack?

Imagine the following scenario: you’re running a small corporate website, and suddenly, your service becomes unreachable, throwing a 503 (service unavailable) Http error at your customers and website visitors. The irritated messages start flooding in to support.
Worried, you walk through the usual administrative checks, to make sure it’s not what you think it is. Is the WebHost up? You check with https://downforeveryoneorjustme.com/ to verify that it’s not a network problem, or that the account hasn’t been disabled. Next, you check for any messages from your web hosting provider, to ensure that you weren’t taken offline for billing, legal, or other reasons. Failing to see any problems there, you then check your host’s website, and subsequently run a traceroute to your hosting company to ensure the problem isn’t with them. When that isn’t the case, you try visiting other sites with content like yours to make sure that you’re not being censored or blocked. You also try accessing your site anonymously with Tor or Psiphon, to rule out this possibility. Nope. Same error.
Fortunately, you’d already configured your Time to Live (TTL)—to 1 hour (rather than the default 72) and you’re able to configure your Response Rate Limiter (RRL) to limit the number of outgoing requests your server will send. You close the connection and reboot, making adjustments to your DNS on CloudFlare, and, eventually, your site comes up again.
Thinking back a bit, you recall your young CEO going off the rails and making some very divisive remarks in a series of interviews that triggered a nasty war of words on Twitter. More than likely, the problem is what you think it was—you’ve been DDoSed. More on the subject:
So what just happened? A denial of service (DoS) attack is where a massive number of requests are directed at a specific target from one (or many) hosts. Once the target’s capacity for handling requests is exhausted, it becomes incapable of handling any more.
However, since the days of broadband, using a single machine for attack stopped working so well. Enter the Distributed Denial of Service Attack (DDoS). A DDoS attack involves hundreds of computers on the internet targeting a single, target “victim” machine.
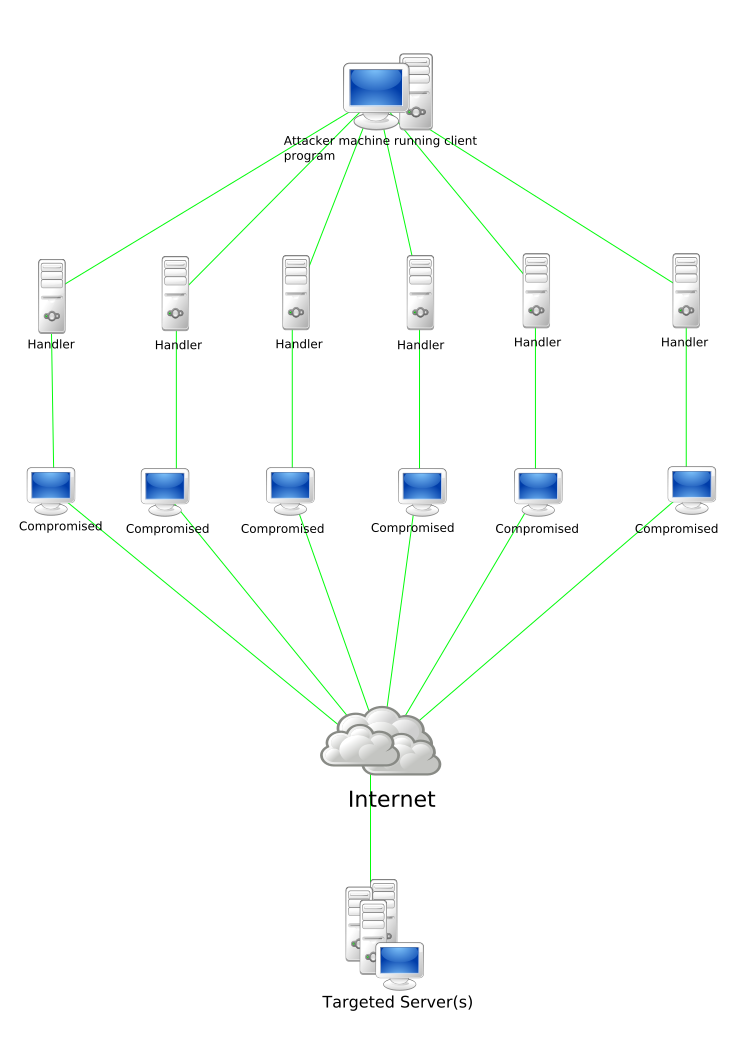
Stacheldraht attack diagram, courtesy of Wikipedia
So how does a botnet work? The typical scenario works something like this: a botnet creator creates—and script kiddies, or various other bad actors deploy—a network of automated self-replicating bots on sometimes hundreds of thousands of unsuspecting user’s machines. These bots operate as background processes, installed, and running silently, listening for commands.
Often, these background processes idle, waiting for a script kiddie to download and run a script to issue them instructions. Upon receiving these commands, these bots then coordinate an attack on a specific target.
But how are these bots installed to unsuspecting users’ machines in the first place? Typically via a few different vectors:
- Users downloading and attempting to decrypt or install malware disguised as (or embedded in) porn, movies, pictures, or compressed executables from even legitimate download sites;
- Users opening malicious attachments;
- Users clicking malicious links or visiting malicious sites; often bad sites which offer an “X” or an “exit” button that actually also installs and initiates the bots.
Many have said that using the Tor network can similarly offer ways for bad actors to take control of your machine and use it toward a botnet attack: either by making malware available via the network, or when the network itself takes over the computer. Users agree to become part of the peer-to-peer network—and lend CPU resources—when they use Tor.
But DDoS attacks need not run via bots. Network stress tools can be coordinated by users themselves to attack a target. This is a good way to understand how the attacks work.
Used in the 2010 attacks by Anonymous on the Church of Scientology, Low-Orbit Ion Cannon (LOIC), is an open-source network stress-testing and DoS attack tool. When used for DDoS attacks, it overwhelms its victim with TCP or UDP packets.
High-Orbit Ion Cannon, a GUI-enabled, IP-anonymizing replacement, appeared in the legal pressure-filled wake of Operation Payback. HOIC can attack up to 256 URLs at the same time using an HTTP flood and requires less coordination between users—at least than its predecessor did—to attack more effectively.
It’s worth noting that anti-virus or malware often won’t catch DDoS malware, as (with any virus) the anti-virus signatures may not exist if the malware is new, or, the anti-malware may not detect malicious behavior if the bot is sending relatively few requests.
Recent Examples
For a filterable, real-time visualization of attacks happening right now, go to https://cybermap.kaspersky.com/
One notable campaign of attacks this year were zero-day exploits targeted at Microsoft Office online. By leveraging at least two known vulnerabilities, attackers used Microsoft Word as a vector to “exploit Adobe Flash Player and Internet Explorer,” even if the former is blocked at most companies, and the latter isn’t the default browser.
While all of 2017 brought 214 zero-day threats, according to Fortinet’s “Threat Landscape Report Q1 2018,” there were 45 in Q1 2018 alone. Along with zero-day threats, malware continues to evolve, along with IoT risks and crypto-jacking.
During Q2 2018 alone, non-standard amplification methods for attacks tended to grow. In the case of the UPnP (universal plug and play) protocol attack, blocking was thwarted as malicious traffic originated from several ports instead of one. Additionally, new botnets are emerging on IoT devices, notably the one based on 50,000 surveillance cameras in Japan. Also, in May, Verge cryptocurrency mining pools were targeted, along with the Bitfinex exchange in June.
Attack Vectors and General Types of Attacks
So, what is the general mechanism of a DDoS attack? Using a botnet, an attacker strives to overload a target with requests so that it can no longer serve legitimate requests. A typical attack vector is via Http to an external IP address, although there are other protocols as well, with UDP being one of the main ones.
Attackers may choose among the following:
- to take advantage of a known vulnerability in the target.
- to saturate the victim’s internet connection. By faking packet requests, for example, attackers can massively spam a port to overwhelm a connection.
- a spoof (a fake origin address) to saturate uplink and downlink. This can involve forcing the victim machine to repeatedly respond with a “ping” to a spoofed IP address.
- to saturate disk, CPU cycles, or memory.
Attacks typically exploit a victim’s external IP addresses, saturating both the download and upload channel.
According to F-Secure, there are 4 basic types of DoS attacks. Let’s look at them, along with some examples of each.
1. Exploit-Based DoS
An “exploit-based” attack exploits a Common Vulnerability Scoring System (CVSS) -ranked vulnerability in the target. In this sort of attack, an attacker sends a malformed packet or request that will either crash or hang the target system. To be effective, the attacker must know of an exploit vector in the target that has not yet been patched. The attacker need only send such a packet now and then to keep the target offline, thus evading detection by host anti-malware.
Exploit-based DoS attacks are generally hard to detect; if the attacker is using multiple hosts, each host need only rarely send a DoS packet.
Zero-day exploits are among the best examples of these.
2. Traditional Flooding DoS
Traditional flooding simply sends traffic in such high volume that a target’s network connection is saturated. A SYN flood is perhaps the most common example of flooding DoS, but any traffic works as long as it reaches the target.
TCP floods, SYN floods, and UDP floods (including ping floods) are all notable examples.
3. Amplified-Flooding DoS
When an attacker has found an open relay service they can use as a force multiplier, then he can trigger an amplified-flooding DoS. An amplified flooding DoS abuses protocols that use UDP. One such method involves forged NTP time protocol queries; the response address is forged with the victim’s address as the response address. Since the original request is much smaller than the (amplified) reply, the victim may ultimately receive up to 200x the amplification that the attacker originally sent.
Arguably, amplified attacks are the most common these days, because of their effectiveness. Here are a few examples of protocols and methods that have been used in amplification attacks:
- CharGEN floods;
- SNMP floods;
- NTP floods;
- SSDP floods;
- SNMPv2;
- QOTD;
- BitTorrent;
- Steam Protocol.
4. Resource-Consumption DoS
A resource consumption DoS is the most problematic attack type. However, as it requires the attacker to spend some time understanding the target, it’s probably the rarest sort. In a resource-consumption attack, the attacker writes either a custom tool or uses one capable of interacting with the target to consume resources, causing a slowdown or eventual freeze up of the target system.
Note that any of these exploits can be a simple single-attacker denial of service, but most are distributed nowadays.
Call to Action
We’ve just learned what DDoS means and walked through some recent and well-known cases. We’ve also looked at the different types of attacks as well and drilled down to a few specific examples.
But how do you avoid becoming part of a botnet? How do you mitigate against future attacks? And what do you do when attacked? Logz.io can help you monitor your perimeter to check for anomalies in your network traffic. Check our next article for more.
Get started for free
Completely free for 14 days, no strings attached.