
Correlate CrowdStrike Data with Logz.io Cloud SIEM
July 7, 2021

Crowdstrike is an innovator in the endpoint protection market with innovative approaches for the last decade. They specialize in depth of data collection and have uncovered many forensic mysteries in security over the last 10 years. We have many mutual customers with CrowdStrike, which is why we began working with them on a solution to analyze and correlate their data within Logz.io. The endpoint is a critical data source, but without the correlation, it’s a small part of the overall threat landscape.
With Logz.io Cloud SIEM, this data can be analyzed and correlated with other threat data. Logz.io includes rules which fire alerts based on best practices which defined in our out of the box rules, along with visualizations in the included Dashboards for CrowdStrike. These can be changed by the users to fit their specific needs and environments.
More on the subject:
The alerts provide notifications or automation as defined by the user of the SIEM based on the detection of malicious files, policy changes, updates, and other suspicious activity on the command line. These allow the SecOps team to see activity in context of the other security signals that have been collected across the organization, then to take the corrective action. Here are the rules in our alerting system:

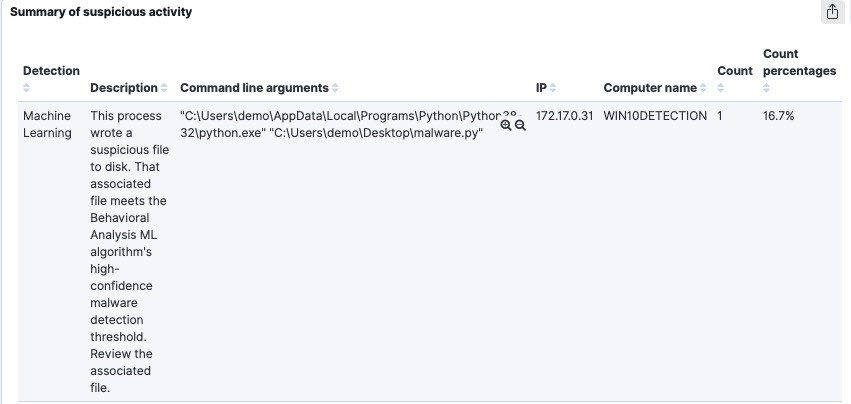
Here is a summary of detected activity coming from CrowdStrike:
CrowdStrike provides the Falcon SIEM Connector, which collects data from the SaaS streaming Endpoint. We, we then send this data using the CNCF project Fluentd to send the log data to Logz.io. We have included operational dashboards which provide a lot of insight into what is currently happening across multiple CrowdStrike instances and systems.
CrowdStrike Dashboard
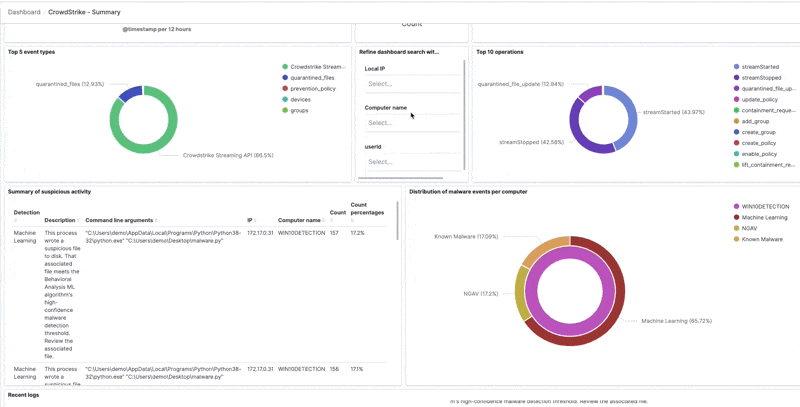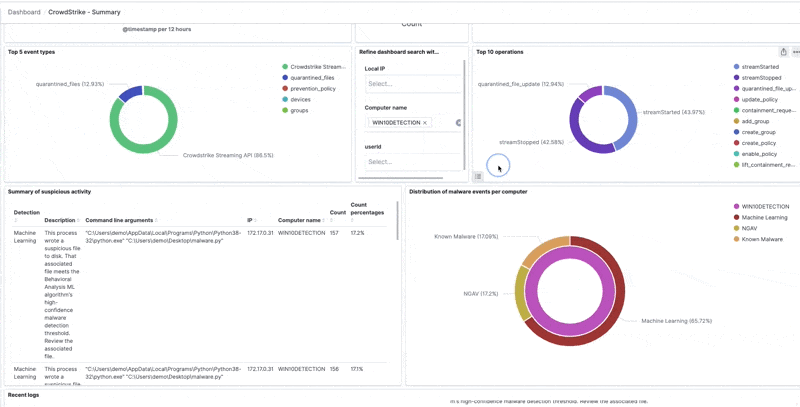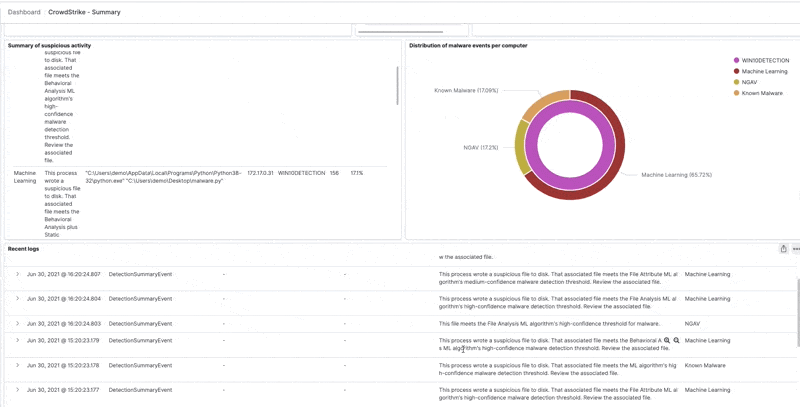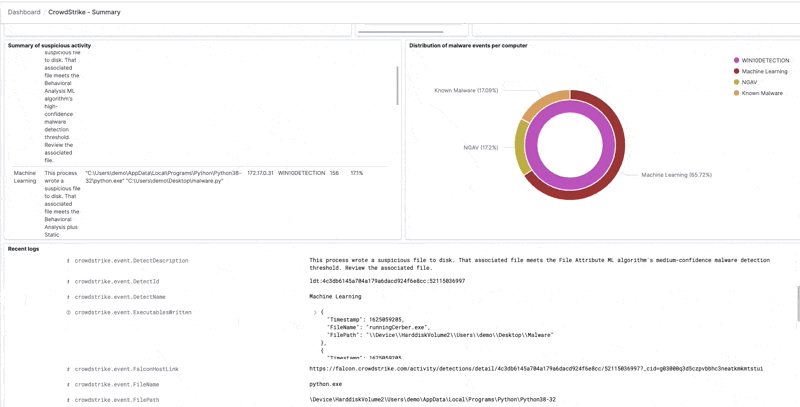
The overall dashboard includes the following sets of data:
- Showing the number of logs over time, which allows for identification of problems that spike the log volumes.
- Event status of logs view shows the event types over time. These are based on the value of the “status” field and if the operation/\event succeeded or failed. We count all of those values and showing total count of how many events are collected for a given type.
- Top event types – Shows the top 10 “operations” running in the environment
For example “twoFactorAuthenticate” and “detection updates” along with other types of events which are noisy.
- Suspicious activity table – shows the suspicious activity detected by the agent, and shows the most important details. For example, cCredential theft, or suspicious activity. The details are also included for example “user password hash was dumped” and we will also extract the command line arguments. We also show that the IP and hostname are related.

Drilling down on a specific computer name, IP address, or hostname is done easily to see the correlated data collected by the Logz.io Cloud SIEM from CrowdStrike and other data sources:
We appreciate the assistance of the CrowdStrike partnership team in working with us on this integration. A special thanks to the Logz.io integration team who put together the solution. We have many mutual customers, and we believe that this will add additional value. If you have any suggestions or questions about this please reach out to us, or contact me directly @jkowall on Twitter or via LinkedIn.




