Investigate Stormshield & SonicWall Events with Logz.io Cloud SIEM
October 21, 2020

Stormshield and SonicWall are popular firewalls used to monitor network traffic for malicious actors. Firewalls can help detect all kinds of attacks, like brute force logins, DDoS, and SQL Injection, but they just make up a piece of the security puzzle.
Most teams will have many other security tools that address different kinds of vulnerabilities and attacks. The result can be a cacophony of alerts for ‘high priority’ attacks at a given time – making it difficult to know where to start.
That’s why tools like Logz.io Cloud SIEM exist: to collect, prioritize, and investigate security events from a wide variety of tools so that security teams can effectively respond to the greatest threats.
Now, you can integrate Logz.io with SonicWall and Stormshield. When these firewalls detect security events, they will send logs recording the events to Logz.io to be parsed and displayed on a security dashboard for prioritization within the larger security context. The first step is to set up the shipping method from the firewalls to Logz.io.
Ship Your Logs to Logz.io
For both Stormshield and SonicWall, we can ship their logs to Logz.io with FileBeat – a lightweight open source log shipping agent. The steps are nearly the same for both:
- Download the Logz.io public certificate to your Filebeat server
- Configure Filebeat’s settings (codeblocks in documentation)
- Set Logz.io as the output by entering your Logz.io shipping token and listener host
- Restart Filebeat
For SonicWall, you’ll also need to configure SonicWall Server logging to send logs to the Filebeat server
For the complete instructions and the codeblocks for Filebeat’s configuration, see our documentation for Stormshield and SonicWall .
Stormshield Rules and Dashboards
To help you make sense of Stormshield’s results, we’ve built rules and dashboards to help you identify and visualize the most critical threats.
Some of Stormshield’s rules are based on authentication. “Failed authentication from a malicious address was detected” is triggered whenever the threat intelligence finds a malicious IP in a failed authentication attempt log.
“Multiple users failed authentication from a single IP address” can be a strong indication of a brute force login attempt or use of a proxy server in your environment. In this case, you can use Stormshield to block the IP address of the suspicious actor.
Other rules are based on Stormshield’s IPS (Intrusion Prevention System) policies. There is a rule that triggers whenever the IPS detects a malicious actor trying to gain access to your systems. But there are other indicators that impact the severity of a violated IPS policy For this reason, there are additional higher severity rules when a violated IPS policy comes from a malicious address or multiple violated policies come from a single address.
In addition to rules, Logz.io has also built dashboards to help you monitor and visualize the security events identified by Stormshield. At the top of the dashboard, you can filter all of Stormshield’s logs by source and destination IP addresses.
From all of these findings from stormshield (represented by each log), we can quickly see the most interesting events in the ‘Triggered rules’ visualization.
You can filter in these events to investigate them further.
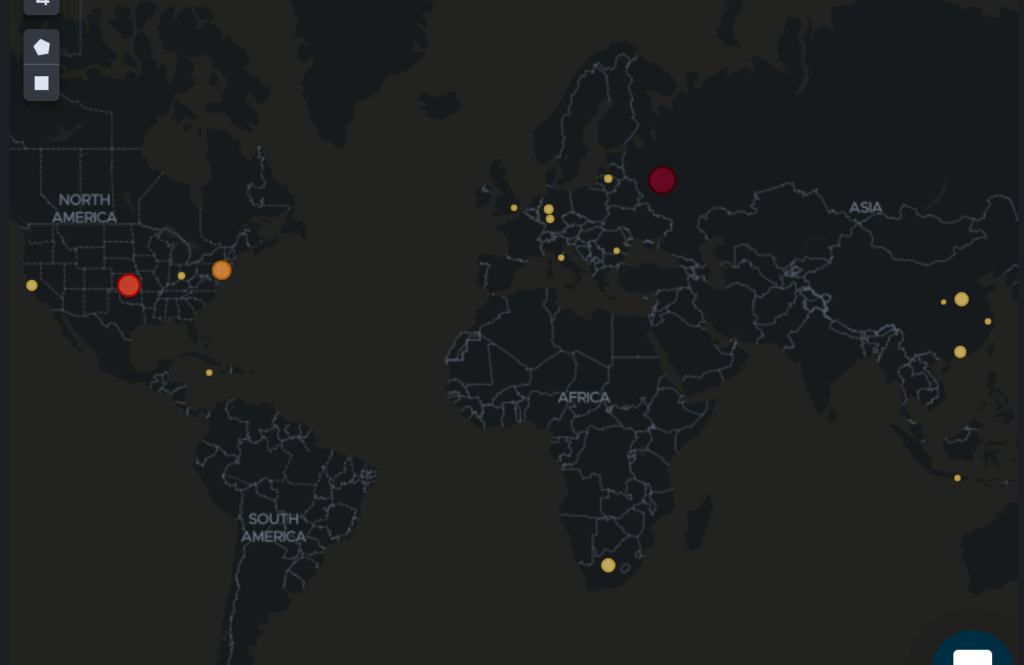
From here, the dashboard slices the logs into different categories to help you prioritize and investigate the most interesting findings. For example, you can view the logs by port or protocol…
…as well as geographical information…
SonicWall Rules and Dashboards
If you’re using SonicWall, you can benefit from the pre-built log parsing, rules, and dashboards provided by Logz.io Cloud SIEM. This way, you can focus your attention on the most interesting results in the context of your larger security strategy.
For example, we’ve built a few rules to highlight failed authentication attempts discovered by SonicWall. After all, an attacker could wreak havoc with control over your firewall. There are multiple rules for failed authentication attempts into SonicWall with varying severities depending on whether the failed attempts came from a single or malicious source.
SonicWall is also built around an IPS, so there are many rules based on violated IPS policies that indicate attacks. After these rules are triggered, next steps would be to ensure SonicWall blocked the attack. If it looks like there was a breach, you can use SonicWall to block the IP address.
You can visualize violated IPS policies in the SonicWall monitoring dashboard.

SonicWall dashboard and graph detecting IPS signatures, Logz.io Dashboard
Other SonicWall rules flag port scanning activity, multiple connection attempts from a remote access port, and connection to a malicious IP address from within your organization.
In addition to correlating incoming SonicWall logs with rules, Cloud SIEM also highlights specific logs with malicious IPs by cross referencing logs with threat intelligence feeds. Users can investigate these logs and see where they’re coming from on the SonicWall monitoring dashboard.

Logz.io Cloud SIEM highlights specific SonicWall logs for malicious IPs
And of course, protecting authentication and authorization for SonicWall itself is important, so you can view the login attempts by role to spot any suspicious login activity.

User failed logins by login types on the SonicWall Logz.io Cloud SIEM dashboard
Focusing on What’s Important
Tool sprawl is real for security teams. More tools mean more UIs, more learning curves, and more alerts. Logz.io Cloud SIEM makes findings from StormShield, SonicWall, and many other security tools easy to consume and understand by providing rules and monitoring content to surface the most important information.
Looking to give it a shot? Request a demo to see it for yourself.