
The Top 5 Open-Source NIDS Solutions
April 11, 2019

In a hyper-connected world, the threat landscape is undoubtedly evolving. Ensuring the security of your enterprise networks on a daily basis is essential to protect your business, no matter how big (or small) it is. According to SophosLabs’ 2019 threat report, one dangerous ransomware called SamSam cost companies $6.5 million ($10K to $50K per ransom). This threat used vulnerable services (RDP, FTP, etc.) to gain access to networks and caused damage even to governments of big cities such as Atlanta, where many city services were attacked including court services. More on the subject:
In order to improve the visibility of malicious network activities in your network and hybrid environments, and to avoid similar situations, it is important to deploy network-based intrusion detection systems, or NIDS. Such systems are usually deployed alongside host-based intrusion detection systems, or HIDS, enabling you to gain information about incoming and outgoing traffic from the internet. This information, in turn, gives you the ability to identify the latest advanced persistent threats quickly and stop them before they exfiltrate PII and other sensitive data.
In this article, we’ll explore five significant open-source network-based intrusion detection systems to help you enhance threat visibility across your networks.
About NIDS
Host-based intrusion detection systems trace the hosts’ behaviors for any suspicious activity by examining events on your hosts. Network-based IDS, on the other hand, analyze network traffic for any intrusion and produce alerts to system administrators and network security engineers. In other words, NIDS complements HIDS to enforce detection–both signature-based and anomaly-based – and acts as a safeguard to monitor traffic going to and from your organization’s different network devices.
Intrusion detection can be very expensive. So we selected the most significant open-source and free intrusion detection systems to help you protect your network from data theft and unauthorized access as well as help you identify the most critical threats.
1. Snort
Snort is a free and open-source network-based intrusion detection system maintained by Cisco Systems. It is the most-known tool in the open-source market, runs on different platforms including Windows and Linux, and is able to analyze real-time traffic.
Snort operates under three different modes: sniffer mode, packet logger, and intrusion detection. The intrusion detection mode is based on what is called “base policies,” which are simply a set of rules. You can also add your own rules freely, or you can just download the rules developed and shared by the Snort community. This community is a great resource, with a wide range of fellow engineers and experts who are very supportive. You should always make sure to visit the Snort forums to check for any new shared rules and policies.
The intrusion detection functions of Snort are able to detect OS fingerprinting, port scanning, SMB probes, and many other different attacks via two detection methods: signature-based and anomaly-based techniques.
Snort does come with some shortcomings. The graphical user interface is not very user friendly, even though many GUIs were made and introduced by the community to solve this issue. Also, the operation of processing packets can be slow and overwhelming. Lastly, you need to be careful when you create your own rules to reduce false positives.
The following workflow describes how snort works:
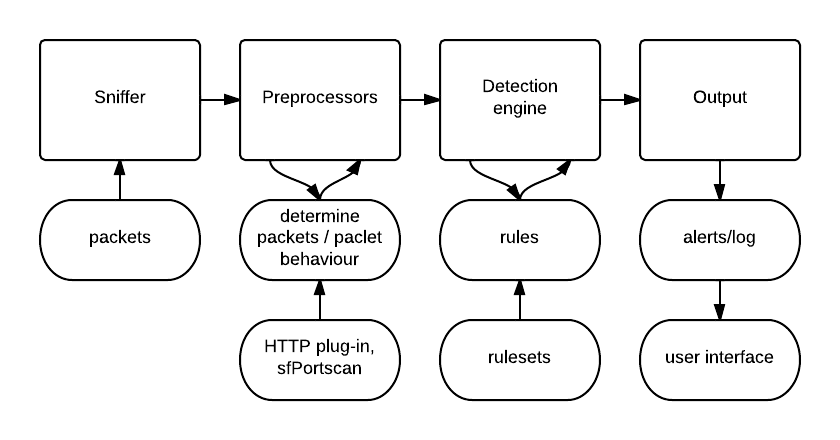
Figure 1 (Image Source)
2. Suricata
Suricata is another free open-source network-based intrusion detection system. As its official documentation indicates, Suricata provides real-time intrusion detection and prevention capabilities in addition to features for monitoring network security. Thus, Suricata can act as a complete network monitoring ecosystem. It is also compatible with Snort’s data structure, and you can even implement Snort policy bases inside Suricata for added convenience.
This system goes beyond network intrusion detection to examining TLS certificates, HTTP requests, and DNS transactions. To ensure good integration with other solutions, such as SIEMs and databases, Suricata uses YAML and JSON files as inputs and outputs. Suricata’s workload is also distributed thanks to its multithreading capabilities and GPU acceleration.
All of these powerful capabilities do come with a price, as you need intensive resources to run the project smoothly.
The following screenshot illustrates the Suricata dashboard in the intrusion detection mode:

Figure 2 (Image Source)
3. Zeek
The Zeek (formerly Bro) Network Security Monitor is also free and open-source. As its name indicates, this NIDS is more than a network intrusion detection system because it also provides monitoring capabilities. Zeek can run on Unix, Linux, and Mac OS and follows two operations: first traffic logging, managed by an event engine, and then analysis. This project differs from Snort due to the fact that it also runs on the application layer. In other words, Zeek gives you the ability to track different services from different OSI layers, such as HTTP, DNS, SNMP traffic, and FTP, thanks to a variety of protocol-specific analyzers.
Like other NIDS solutions, Zeek does use signature-based and anomaly-based detection methods. The project is also supported by a vast and diverse user community, with contributors from various backgrounds (academia and industry) as an added benefit. This IDS, however, comes with some limitations, as it typically needs a good amount of effort to deploy along with solid programming and scripting skills to handle it proficiently.
4. OpenWIPS-ng
OpenWIPS-ng is a free open-source NIDS dedicated to wireless networks–WIPS stands for wireless intrusion prevention system. This tool was developed by the same team that developed the well-known network intrusion tool Aircrack-ng.
You can use OpenWIPS-ng either as a WiFi packet sniffer or for intrusion detection. OpenWIPS-ng works exclusively on Linux systems and comes with three major components:
- A sensor to collect data and send out commands.
- A server that contains the analysis engine.
- An interface to display the events and alerts.
Most of the processing runs on the server since most of the plugins are running there, and the packets are reassembled there as well. The communication is encrypted by default and is handled by two types of channels: command and data.
This NIDS does have some limitations. Every installation includes only one sensor, and each sensor contains small CPUs. In addition, the sensors do not always detect the same traffic.
The following diagram illustrates the architecture of OpenWIPS-ng project:
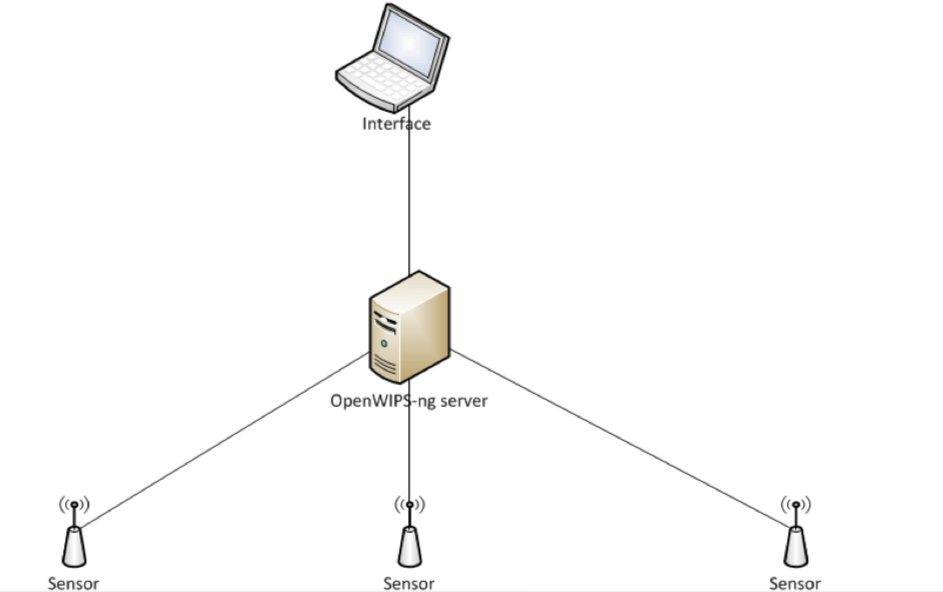
Figure 3 (Image Source)
5. Sguil
Sguil is a collection of components for Network Security Monitoring developed by Robert “Bamm” Visscher under a GPLv3 license. The current stable version of Sguil is 0.9.0, and, as with any other NSM, its role is collecting and presenting data to analysts who can then detect and respond to intrusions.
This client is written in tcl/tk, so it can run on any operating system that supports this programming language, including Linux, BSD, Solaris, Mac OS, and Win32. You can also configure it by modifying the /etc/sguil/sguil.conf file. After installing Sguil, analysts can receive alerts, including from Snort, Suricata, OSSEC, Bro, and many other data sources. They can also categorize events and alerts and even forward events and alerts to senior management.
Sguil will definitely help you reduce intrusion-detection time–from five hours to 45 minutes, according to Vorant Network Security, Inc. This is a solution with good capabilities, but you do need to keep in mind that the client can only utilize 1,024 sockets for receiving communication from the different agents.
The following screenshot illustrates a Sguil sancp query:
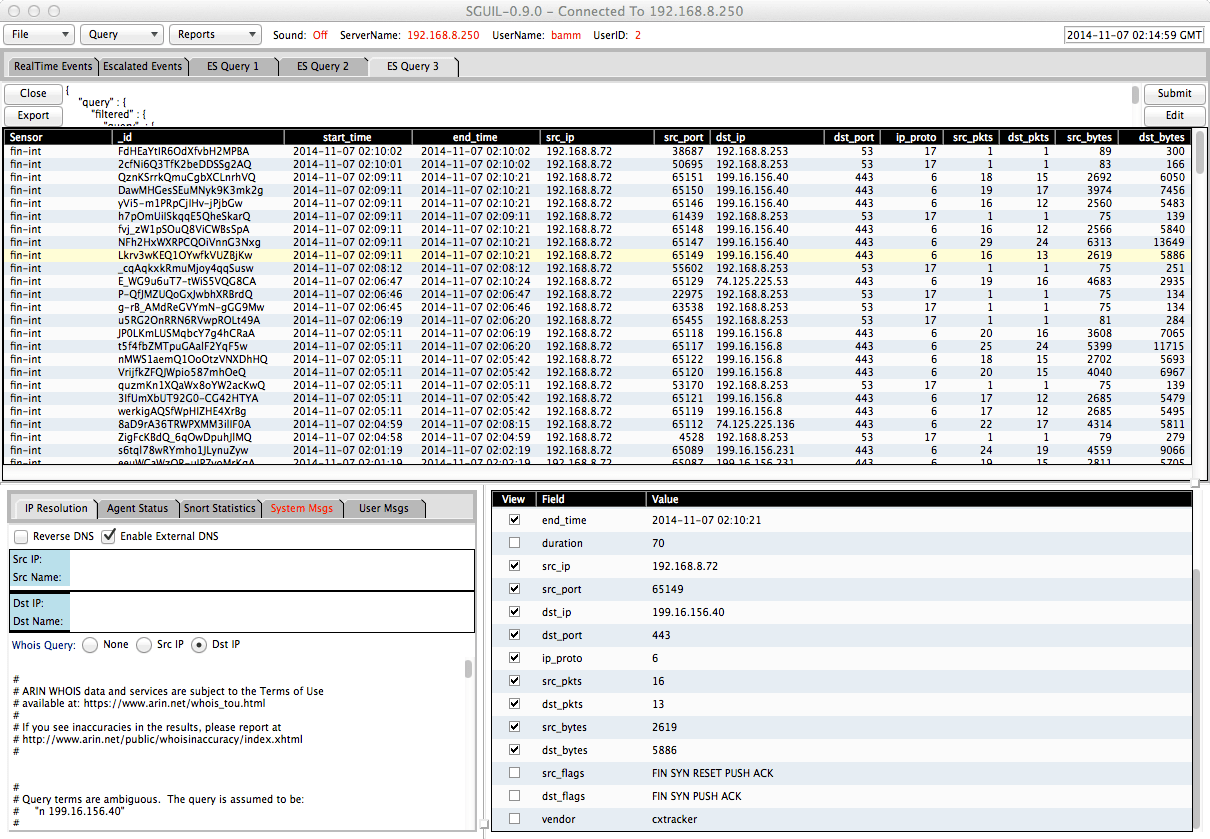
Figure 4 (Image Source)
Summary
This article reviewed five open-source network-based intrusion detection systems that are the most well-known in the sector today. Now, you should have a clearer understanding of both the advantages and limitations of each one of these systems so as to help you select the most suitable safeguard for your network.
For more tips on best practices and tools for your security operations, check out our Complete Cloud Operations Security Blueprint.




